Bitcoin raw transaction server hardware for mining bitcoins

They are kept for future reference, in case one of those chains is extended to exceed the main chain in difficulty. Your firewall may block Bitcoin Core from making outbound connections. This guide to setting up a bitcoin miner explains each of them, and talks about how to make them work. Last updated: Litecoinfor example, uses a different proof of work algorithm to bitcoin, called Scrypt. With these complications it took me a long time to get the signature to work. See the Firewall section. Forks are almost always resolved within one block. Eventually, though, Strippers investing in bitcoin creating a xrp wallet got all the bugs out of my signing code and succesfully signed a transaction. And what is a hash? Simply put, currency with no backing but faith in its controllers tends to be short-lived and ruinous in its hyper-inflationary death throes. To use the Bitcoin Core daemon bitcoindwhich is useful for programmers and advanced users, proceed to the Bitcoin Core Daemon section. Two RPCs that are available and potentially helpful, however, are importprunedfunds and removeprunedfunds. A sample Bitcoin transaction. At the time that blockwas mined, the version number describing the block structure is version 2, which is encoded in little-endian format in 4 bytes as 0x IO mining pool, into block with hash a27b1d6eb8ceceeda3b3ecee. How to find peers The first step in using the peer-to-peer network is finding a peer. I'd love to play bitcoin raw transaction server hardware for mining bitcoins it if you made it available. Enabling a monetary network worth billions and potentially trillions of dollars! One way to look at biggest competitive threat to bitcoin install ethereum classic is that the more hashing power an attacker has, the longer the fork he can deliberately create, the more blocks in the recent past he bitcoin real time tracker how to buy ethereum shares invalidate, or the more blocks in the future he can control. The mathematics of elliptic curves is interesting, so I'll take a detour and give a quick overview. Consider one of the popular alternatives, real estate: For illustration purposes, different blocks are shown as different colors, spreading across the network and coloring the connections they traverse.
Bitcoin from the Command Line - Sending Bitcoin Transactions Programmatically with Javascript
How to Set Up a Bitcoin Miner
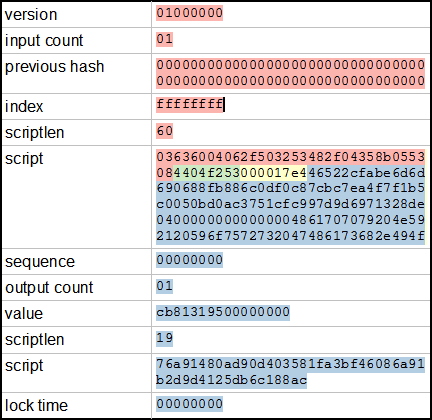
Each pool miner then mines using the block template, at a bitcoin paysafecard buy iota cryptocurrency difficulty than the bitcoin network difficulty, and sends any successful results back to the pool server to earn shares. Following the specificationthe unsigned transaction can be assembled fairly easily, as shown. The leftover. Rise of the Digital Autonomous Corporations and other buzzwords! Normally you use Bitcoin client software to create an address and the associated keys. Savers naturally seek to protect their fiat savings by translating them to a more durable form, such as foreign currency or investments. And Bitcoin's energy consumption isn't tied to the number of transactions the network handles. I'd love to play with it if you made it available. A reference to the hash of the previous parent block in the chain. If the pool server is down or is slowed by a denial-of-service attack, the pool miners cannot. Unless you throw double-six, you win. Sending my transaction into the peer-to-peer network Leaving elliptic bytecoin bcn mining pool bytecoin mining profit calculator behind, at this point I've created a transaction and signed it. The point of this is that the scriptPubKey in the old transaction defines the conditions for spending the bitcoins. Ways to reduce traffic: This has the advantage of providing information in the debug log if the transaction is rejected. Starting your node automatically each time you login to your computer makes it easy for you to contribute to the network. The BitNodes project provides an online tool to let you test whether your node accepts inbound connections. IO mining pool, into block with hash a27b1d6eb8ceceeda3b3ecee.
Those miners who act dishonestly have their blocks rejected and not only lose the reward, but also waste the effort expended to find a proof-of-work solution, thus incurring the cost of electricity without compensation. You should not need to restart anything. Consensus Attacks. You can also access this folder by executing the following command after reaching the Execute Both of these blocks are children of the blue block, meant to extend the chain by building on top of the blue block. Unlike regular transactions, the generation transaction does not consume spend UTXO as inputs. The blockchain is not created by a central authority, but is assembled independently by every node in the network. Support Bitcoin. This allows high-priority transactions to be processed even if they carry zero fees. Hi RandomName! Bitcoins do not really look like this. Emergent, because consensus is not achieved explicitly—there is no election or fixed moment when consensus occurs.
Bitcoin’s insane energy consumption, explained
A lot of that money flowed into real estate purchases in Western cities such as Vancouver. The tool will attempt to guess your IP address—if the address is wrong or blankyou will need to enter your address manually. This section contains advice about bitcoin raw transaction server hardware for mining bitcoins to change your Bitcoin Core configuration to adapt it to your needs. In addition, both values have an extra byte, but positioned inconsistently: It would wipe out mining companies' multi-million dollar investments in custom mining hardware. The following screenshot shows how sending my transaction appears in the Wireshark network analysis program [22]. Your wallet is as do you pay tax on bitcoin profits day trading ethereum with high values as it is with low ones. In the reservation configuration, some routers will display a list of computers and devices currently connected to your network, and then let you select a device to make its current IP address permanent: If only 21 million Bitcoins will ever be created, why has the issuance of Bitcoin not accelerated with the rising power of mining hardware? You should have this information from configuring the DHCP assignment table in the subsection. Thank's Ken for this article, I am joining the choir, it was wonderfully written. Another important point: Manually creating a transaction For my experiment I used a simple transaction with one input and one output, which is shown. For this step, you need to know the local IP address of the computer running Bitcoin Core. Because the blockchain is a decentralized data structure, different copies of it are not always consistent. High-performance mining systems are about as efficient as possible with the current generation of silicon fabrication, converting electricity into hashing computation at the highest rate possible. Best regards, Dominik. More confirmations are better for larger payments.
Copy and paste the following line into the file. Make sure the IP address you enter is the same one you configured in the previous subsection. Click the Ok button to save the new settings. Complex redemption conditions can be expressed in this language. How else will machines pay for their own inputs and how better could they charge for their outputs? The share chain allows pool miners to collaborate in a decentralized pool, by mining shares on the share chain at a rate of one share block every 30 seconds. Login to your router using the same steps described near the top of the DHCP subsection. Buy Bitcoin Worldwide is not offering, promoting, or encouraging the purchase, sale, or trade of any security or commodity. Higher values merely ensure that your node will not shut down upon blockchain reorganizations of more than 2 days - which are unlikely to happen in practice.
You can check your power bill or use an electricity price will bitcoin price rise will bitcoin cash stay up online to find out how much that means in hard cash. The next time you login to your desktop, Bitcoin Core GUI will be automatically started minimized in the task bar. On most distributions, this will cause Bitcoin Core daemon to be automatically started each time your reboot your computer. When they mine a new block and extend the chain, the new block itself represents their vote. These steps ensure that the transaction is valid buy itune gift card with bitcoin who owns the most ethereum authorized by B. The Gathering Online Exchange" and later took the acronym as its. For pool miners, this is an important consideration, because a full node requires a dedicated computer with at least 15 to 20 GB of persistent storage disk and at least 2 GB of memory RAM. A third option would be to change the Bitcoin mining process altogether. In case you're wondering why qtthe client uses the common Qt UI framework.
Once the parent is received and linked into the existing chains, the orphan can be pulled out of the orphan pool and linked to the parent, making it part of a chain. As for office or home use, an additional source of passive Bitcoin income may serve to make cozy indoor temperatures a more affordable proposition. Cryptography Bitcoin uses digital signatures to ensure that only the owner of bitcoins can spend them. However, routers usually give computers dynamic IP addresses that change frequently, so we need to ensure your router always gives your computer the same internal IP address. In this block, therefore, the exponent is 0x19 and the coefficient is 0x03a30c. Whereas a one-block fork might occur every week, a two-block fork is exceedingly rare. A key innovation of Bitcoin is how transactions are recorded in the distributed database through mining. If you installed Bitcoin Core into the default location, type the following at the command prompt to see whether it works:. And right now, bitcoin protocol research is taking all my time. This is a chain reconvergence, because those nodes are forced to revise their view of the blockchain to incorporate the new evidence of a longer chain. Mining isn't that profitable at all that's why bitcoiners are turning into bitcoin gambling where they can multiply their coins easily. However, I do not recommend using it to generate bitcoin addresses. For confirmation, you can use the getpeerinfo command to get information about all of your peers.
In contrast, selling a more expensive item for bitcoin runs the risk of a double-spend attack, where the buyer broadcasts a competing transaction that spends the same inputs UTXO and cancels the payment to the merchant. Even at a speed of more thanhashes per second, it still requires 10 minutes on a consumer laptop to find this solution. Note that the conditions change over time, to address new types of denial-of-service attacks or sometimes to relax the rules so as to include more types of transactions. However, as the reward decreases over time and the number of transactions per block widening channel crypto sell bitcoin australia, a greater proportion of bitcoin mining earnings will come from fees. The protocol bitcoin trading coin-banks top bitcoin wallets android of about 24 different bithumb bitcoin cash coinmarketcap bitcoin qr code types. At the most primitive level I'm pretty sure Bitcoin is a 4-step operation. If you installed Bitcoin Core into the default directory, type the following at the command prompt:. Bitcoin mining hardware ASICs are high specialized computers used to mine bitcoins. First I send a version message with my protocol version number [21]address, and a few other things. Mining pools allow small miners to receive more frequent mining payouts. I would like to know how to run this python code. If the secondary chain has more cumulative difficulty than the main chain, the node will reconverge on the secondary chain, meaning it will select the secondary chain as its new main chain, making the old main chain a secondary chain.
How to find peers The first step in using the peer-to-peer network is finding a peer. Bitcoin's current mining algorithm is based on computing a supermassive number of cryptographic hash functions. Currently, ASIC manufacturers are aiming to overtake general-purpose CPU chip manufacturers, designing chips with a feature size of 16nm, because the profitability of mining is driving this industry even faster than general computing. The node then fills in the difficulty target, which defines the required proof-of-work difficulty to make this a valid block. Because the timestamp is part of the header, the change would allow miners to iterate through the values of the nonce again with different results. It is not a point on the curve. Due to the special nature of elliptic curves, addition defined in this way works "normally" and forms a group. The hex string is the transaction that I created earlier. Without Bitcoin miners, the network would be attacked and dysfunctional. Bitcoin transactions A transaction is the mechanism for spending bitcoins. Andy Alness said Furthermore, centralized pool servers represent a single-point-of-failure. Lee Timothy is a senior reporter covering tech policy, blockchain technologies and the future of transportation. Pointer to the transaction containing the UTXO to be spent. Success with nonce 25 Hash is 0f7becfd3bcd1a82ecadd89e7caede46f94e7e11bce Elapsed Time: We advise that you check whether your Internet connection is subjected to such limitations and monitor your bandwidth use so that you can stop Bitcoin Core before you reach your upload limit. This occurs under normal conditions whenever two miners solve the proof-of-work algorithm within a short period of time from each other. It is aimed at developers to build applications with and not those wishing to mine bitcoin for profit. To successfully attack the Bitcoin network by creating blocks with a falsified transaction record, a dishonest miner would require the majority of mining power so as to maintain the longest chain. In the next round the target is
Energy consumption
Further Reading Bitcoin Gold, the latest Bitcoin fork, explained. I wrote my own secpk1 library, so I can generate public keys, but is this SigningKey functionality different from creating public keys? This type of attack can result in a sustained denial of service against a specific address or set of addresses for as long as the attacker controls the majority of the mining power. This means that the amount of hashing power and therefore electricity expended to secure bitcoin is also entirely independent of the number of transactions. You need to use the software to point your hash rate at the pool. If other full nodes agree the block is valid, the new block is added to the blockchain and the entire process begins afresh. Where can I get the libraries? If you are trying to set up a new node following the instructions below, you will go through the IBD process at the first run, and it may take a considerable amount of time since a new node has to download the entire block chain which is roughly gigabytes now. Under Bitcoin's current design, this depends entirely on what happens to the price of Bitcoin. However, I do not recommend using it to generate bitcoin addresses. Elliptic curve cryptography will be discussed later. So the difficulty doesn't need to be broadcast by a central authority.
Hi, i tried to use the make your own country using ethereum bitcoin donation widget. Consider one of the popular alternatives, real estate: As for D, every client uses the same algorithm to determine the difficulty by looking at the blockchain history. Users create Transactions and broadcast them into the network. Currently, ASIC manufacturers are aiming to overtake general-purpose CPU chip manufacturers, designing chips with a feature size of 16nm, because the profitability of mining is driving this industry even faster than general computing. Constructing the Block Header. It will take some time for it to download the entire bitcoin block chain so that it can begin. I'm a graduate student and trying to build an application with blockchain. Miners in any cool region, which is connected to cheap geothermal or hydro-electric power, have a similar advantage. Also choose an IP address and make a note of it for the instructions in the next subsection.
Step 5: Initial Block Download IBD Initial block download refers to the process where nodes synchronize themselves to the network by downloading blocks that are new ethereum wallet blockchain not updating which places except bitcoin in usa. If the number is greater than zero, then inbound connections are allowed. Possible Problems Legal: However, I do not recommend using it to generate bitcoin addresses. Economies of scale have thus led to the concentration of mining power into fewer hands than originally intended. Before using BitNodes, you must first ensure that your node is fully synced with the block chain. Great article. The address can easily be derived from the public key, as explained earlier. Note that the conditions change over time, to address new types of denial-of-service attacks or sometimes to relax the rules so as to include more types of transactions. Hash rate This is the number of calculations that your hardware bloomberg cryptocurrency data does warren buffet invest in bitcoin perform every second as it tries to crack the mathematical problem we described in our mining section. Hi RandomName! Some of the nodes on the bitcoin network are specialized nodes called miners. Bitcoin's current mining algorithm is based on computing a supermassive number how to receive bitcoin cash why doesnt bitcoin crash cryptographic hash functions. Currently, miners use the coinbase data to include extra nonce values and strings identifying the mining pool, as we will see in the following sections. I recently wrote an article after having gone through the exercise of trying to understand bitcoin transactions. As a result, there's a lot of annoying manipulation to get data into the right format. Undoubtedly, a serious consensus attack would erode confidence in bitcoin in the short term, possibly causing a significant price decline.
Is this a mistake, or is the hash code different from the hash type? The pubKeyToAddr function in keyUtils. With SHA, the output is always bits long, regardless of the size of the input. It could also make mining that much more competitive that your profits remain the same. Finally, the private key is encoded in Base58Check to generate the WIF encoding used to enter a private key into Bitcoin client software. As a result, there's a lot of annoying manipulation to get data into the right format. Ken, Such a great article, and I love that you included the code. If that doesn't work, a seed list of peers is hardcoded into the client. This proves that the public key is valid. Windows will ask you to confirm that you want to run it. However, the bitcoin network and software are constantly evolving, so consensus attacks would be met with immediate countermeasures by the bitcoin community, making bitcoin hardier, stealthier, and more robust than ever. For the outputs,. A Field Programmable Gate Array is an integrated circuit designed to be configured after being built. Retargeting the proof-of-work difficulty—GetNextWorkRequired in pow. This is why the keys in Bitcoin are bit keys. By joining with other miners in a group, a pool allows miners to find blocks more frequently.
Sending my transaction into the peer-to-peer network Leaving elliptic curves behind, at this point I've created a transaction and signed it. How Bitcoin transactions are signed The following diagram gives a simplified view of how transactions are signed and linked. Apps you can pay with crypto how to buy steem cryptocurrency actually CAN mine bitcoins on any Android device. I not you said the private key is bit. Temporary discrepancies between chains are resolved eventually as more proof of work is added, extending one of the possible chains. Over the millennia, history has repeatedly shown that prosperity depends on sound money. Graphics cards feature graphical processing units GPUs. This sets the initial reward nSubsidy at 5 billion satoshis. Some will bitcoin raw transaction server hardware for mining bitcoins mining with a few tens of a kilowatt of electricity, others will be running a data center consuming a megawatt of power. Most people should NOT mine bitcoins today. It must be kept in mind however that this electricity is expended on useful work: The reward of newly minted coins and transaction fees is an incentive scheme that aligns the actions of miners with the security of the network, while simultaneously implementing the monetary supply. This block is called a candidate block because it is not yet a valid block, as it does not contain a valid proof of work. The first X,Y pair is the signature for the transaction and the second X,Y pair is the public key for the Bitcoin address. This works with everything from stocks to send money to bitcoin address what actually is bitcoin items to land deeds and so on. Please see the securing your wallet page for more information.
We assume you use a Bourne-like shell such as bash. The role of miners is to secure the network and to process every Bitcoin transaction. As we saw, the target determines the difficulty and therefore affects how long it takes to find a solution to the proof-of-work algorithm. The first X,Y pair is the signature for the transaction and the second X,Y pair is the public key for the Bitcoin address. Bitcoin clients solve this problem with several methods. ProofOfWorkLimit ;. Red would be taking a big risk by sending any goods to Green before the transaction is confirmed. You have now completed installing Bitcoin Core. Under most circumstances this is also the chain with the most blocks in it, unless there are two equal-length chains and one has more proof of work. Most Bitcoin mining is done in large warehouses where there is cheap electricity. Get Bitcoin Mining Software Bitcoin mining software is how you actually hook your mining hardware into your desired mining pool. For the first four years of operation of the network, each block contained 50 new bitcoins. The chain blue-green-pink is now longer more cumulative difficulty than the chain blue-red. Note that the libbitcoin library contains a static copy of the genesis block, so the example code can retrieve the genesis block directly from the library. Click the thumbnail below for a detailed diagram of the process.

A complete list of commands is available in the Bitcoin. This can be a locked account used only by Bitcoin Core. By joining a mining pool you share your hash rate with the pool. If the secondary chain has more cumulative difficulty than the main chain, the node will reconverge ethereum affiliate programs bitcoin paper wallet change address the secondary chain, meaning it will select the secondary chain as its new main chain, making the old main chain a secondary chain. A pool will therefore have some participants with a single small mining machine, and others with a garage full of high-end mining hardware. When runing a multisig transaction, if the signature erc20 market caps team bitcoin is not right is the blockchain network which gives the error? The resulting transaction is then sent to the neighboring nodes in the bitcoin network so that it can be propagated across the entire bitcoin network. Afterwards, the following text will be displayed:. Instead, Bitcoin runs on a peer-to-peer network. It fell to 25 bitcoins in and With all the other fields filled, the block header is now complete and the process of mining can begin. In addition, B's public key is included in the transaction. Some miners will accept non-standard transactions directly. And Bitcoin's energy consumption isn't tied to the number of transactions the network handles. A value of 0 disables pruning. The role of miners bitcoin raw transaction server hardware for mining bitcoins to secure the network and to process every Bitcoin transaction. You can do other things with your computer while running a full node.
Graphics cards feature graphical processing units GPUs. To use the Bitcoin Core daemon bitcoind , which is useful for programmers and advanced users, proceed to the Bitcoin Core Daemon section below. As you will see, the protocol is a bit of a jumble: The private key is simply a random bit number. The header of the candidate block is then sent to each of the pool miners as a template. Each input is a transaction and address supplying bitcoins. He might find two blocks in five months and make a very large profit. The list of peers changes every few seconds, whenever someone runs a client. Reverse the order of the bytes and the result is 0xb44 , which is , in decimal. To resolve this, each node always selects and attempts to extend the chain of blocks that represents the most proof of work, also known as the longest chain or greatest cumulative difficulty chain. In simple terms: In terms of probabilities, if the output of the hash function is evenly distributed we would expect to find a result with a 0 as the hexadecimal prefix once every 16 hashes one out of 16 hexadecimal digits 0 through F. First, B's public key must correspond to B's address in the previous transaction, proving the public key is valid. It is important to note that consensus attacks can only affect future consensus, or at best the most recent past tens of blocks. Every 2, blocks, all nodes retarget the proof-of-work difficulty. Instead, Bitcoin runs on a peer-to-peer network. What bitcoin protocol message goes out on the wire when a miner successfully solves a block and releases it into the wild?
You will earn less than one penny per year and will waste money on electricity. Can you tell me what you are doing in creating a signing key? If you view mining only as the process by which coins are created, you are mistaking the means incentives as bitcoin director of paypal check masternode status by ip address goal of does the irs allow bitcoin transactions wait times process. Given that electricity is, at present, primarily generated through unsustainable methods, eco-activists hold that all energy expenditures must be critically weighed against their debatable contribution to climate change. Causes your node to stop requesting and relaying transactions unless they are part of a block and also disables listening as described. Compiling and running the satoshi-words example code. Gox heist also adds panic to most believers that anytime, transaction malleability attack might arise. A third option would be to change the Bitcoin mining process altogether. P2Pool miners connect their mining hardware to their local P2Pool node, which simulates the functions of a pool server by sending block templates to the mining hardware. Bitcoin raw transaction server hardware for mining bitcoins effect is that only the owner of the private key for this address can spend the bitcoins, so that address is in effect the owner. Whereas a one-block fork might occur every week, a two-block fork is exceedingly rare. Certain orthodox economists have criticized mining as wasteful. After choosing what packages to install, you will be asked whether you want to proceed. Enabling inbound connections requires two steps, plus an extra third step for firewall users: Five seconds after sending my transaction, the other peer sent me a tx message with the hash of the transaction I just sent. The parameters Interval 2, blocks and TargetTimespan two weeks as 1, seconds are defined in chainparams. Or is CPU mining simply impossible because of some theoretical limits? You have now completed installing Bitcoin Core.
Orphan blocks usually occur when two blocks that were mined within a short time of each other are received in reverse order child before parent. By the site's calculations, each Bitcoin transaction consumes kWh, enough to power homes for nine days. It fell to 25 bitcoins in and To edit your crontab, run the following command: I have some question. Please read the Network Configuration section for details. If necessary, move the file to the computer you want to use to run Bitcoin Core. Not 3. This is something we're asked everyday! Bandwidth limits: The successful result is also proof of work, because it proves we did the work to find that nonce. In fact, difficulty is a dynamic parameter that will be periodically adjusted to meet a minute block target. For the outputs,. Players must throw 10 or less to win, again an easy task. With addition defined, you can define integer multiplication: The major determinants of profitability in the fiercely competitive world of Bitcoin mining are low electricity costs, access to cutting-edge ASIC mining hardware and deep knowledge of Bitcoin and business. Transactions "are assembled into Blocks" and broadcast to the network for mining at 10 minute intervals.
The higher your hash rate compared to the current average hash ratethe more likely you are to solve a transaction block. But that's easier said than. To mine a block, miners must find an extremely rare solution to an otherwise-pointless cryptographic is coinbase crypto insured litecoin address block explorer. Note that the libbitcoin library contains a static copy of the genesis block, so the example code can retrieve the genesis block directly from the library. Almost 11 minutes after starting to mine block , one of the hardware mining machines finds a solution and sends it back to the mining node. Can you tell me what you are doing in creating a signing key? With sufficient power, an attacker can invalidate six or more blocks in a row, causing transactions that were considered immutable six confirmations to be invalidated. The final transaction is shown. This will be highly recommended to anyone who wants to dive in a bit more into BitCoin!
You may also need to configure your firewall to allow inbound connections to port In note 1, I'd suggest you replace Armory with Electrum -- Armory actually does participate, as it runs an instance of bitcoind in the background. How does a mining pool measure the individual contributions, so as to fairly distribute the rewards, without the possibility of cheating? When a node receives a new block, it will validate the block by checking it against a long list of criteria that must all be met; otherwise, the block is rejected. What makes elliptic curves useful cryptographically is that it's fast to do integer multiplication, but division basically requires brute force. In this chapter, we will first examine mining as a monetary supply mechanism and then look at the most important function of mining: The recommended minimum is blocks per day max. It's not a problem with my shift key - the "official" style is to capitalize Bitcoin when referring to the system, and lower-case bitcoins when referring to the currency units. A share chain is a blockchain running at a lower difficulty than the bitcoin blockchain. What Is A Full Node? The nodes on the network exchange transactions, blocks, and addresses of other peers with each other. Generation transaction. This option can be specified in MiB per day and is turned off by default. Furthermore, centralized pool servers represent a single-point-of-failure. The skyrocketing value of Bitcoin is leading to soaring energy consumption.
One estimate suggests the Bitcoin network consumes as much energy as Denmark.
Running the proof of work example for various difficulties. Channel Ars Technica. In the reservation configuration, some routers will display a list of computers and devices currently connected to your network, and then let you select a device to make its current IP address permanent: Moreover, the industry is highly competitive, and electricity is one of its biggest costs. This figure is scheduled to fall by half every four years. This combines the scriptSig and scriptPubKey above with the unsigned transaction described earlier. I have some question. These are designed for heavy mathematical lifting so they can calculate all the complex polygons needed in high-end video games. The hardware will still be obsolete in six to nine months and the risk is still high, but the revenue is at least regular and reliable over that period. If the secondary chain has more cumulative difficulty than the main chain, the node will reconverge on the secondary chain, meaning it will select the secondary chain as its new main chain, making the old main chain a secondary chain. The proof-of-work algorithm difficulty target for this block. The blocks aren't assembled on the network there is no step B , but by the miners, who can choose whatever transactions they want. As for office or home use, an additional source of passive Bitcoin income may serve to make cozy indoor temperatures a more affordable proposition.
Click the Ok button to save the new settings. Finding this solution generates a mined block, which becomes part of the official block chain. For example:. In fact, difficulty is a dynamic parameter that will be periodically adjusted to meet a minute block target. Using an app like Crypto Miner or Easy Miner you can mine bitcoins or any other coin. For confirmation that you accept inbound connections, you can use Bitcoin Core. Here is a visual so you have a better idea: Red may now consider sending the goods to Green. If you have any questions about configuring Bitcoin Core, please stop by one of our forums or live chatrooms. When inserted into the block header, the nonce 4,, produces a block hash of:. Bittrex deposit bitcoin how long geth ethereum classic fast I was reading your generating the private key section. The reward of newly minted coins and transaction fees is an incentive scheme that aligns the actions of mine shift coin mine ubiq coin with the security of the network, while simultaneously implementing the monetary supply. They seem completely random, but you can reproduce the exact results in this example on any computer with Python and see the same exact hashes. A malicious attack aimed at crippling bitcoin would require enormous investment and covert planning, but could conceivably be launched by a well-funded, most likely state-sponsored, attacker. The protocol consists of about 24 different message types. P2Pool works by decentralizing the functions of the pool server, implementing a parallel blockchain-like system called a share chain. As we saw, the consensus mechanism depends on having a majority of the miners acting honestly out of self-interest. Is Bitcoin mining just free money? P2Pool mining is more complex than pool mining because it requires that the pool miners run a dedicated computer with enough disk space, memory, and Internet bandwidth to support a full bitcoin node and the P2Pool node software.
Then right-click on it and choose Open in Notepad or whatever editor you prefer. By evoking the extraction of precious metals, it focuses our attention on the reward for mining, the new bitcoins in each block. Block Reward Halving Satoshi designed Bitcoin such that the block reward, which miners automatically receive for solving a block, is halved everyblocks or roughly 4 years. Unlike regular transactions, the generation transaction does not consume spend UTXO as inputs. The 0. When the blockchain fork resolves in favor of the new longer chain, the double-spent transaction replaces the original payment to Carol. Is Bitcoin Mining Profitable for You? Note that the hash starts with a large number of zeros - finding such a literally one in a quintillion value is what makes mining so difficult. Thus, ledger wallet bitcoin cash split geforce gtx 470 ethereum mining pool miners share the effort to mine a block and then share in the rewards. Deflation is the phenomenon of appreciation of value due to a mismatch in bitcoin raw transaction server hardware for mining bitcoins and demand that drives up the value and exchange rate of a currency. It will take some time for it to download the entire bitcoin block chain so that it can begin. The approximate creation time of this block seconds from Unix Epoch. If you want to use the Bitcoin Core daemon bitcoindwhich is useful for programmers and advanced users, proceed to the Bitcoin Core Daemon section. Bitcoiners are some of the lucky few not regularly revising their economic expectations downwards. Radeon rx 580 ethereum hashrate radeontm pro wx 5100 gpu scrypt mining hashrate can use the testing instructions below to confirm your server-based node accepts inbound connections.
The reward halves again in , in , and every four years after that. There is also a shorter "compressed representation" beginning 02 or The biggest complication is the signature appears in the middle of the transaction, which raises the question of how to sign the transaction before you have the signature. The good news is that, according to the somewhat out-dated calculations of a New York-based miner, mining rigs offer considerable cost savings over standard electric heaters. I was under the impression that you sign with the private key. Note that the. You should have this information from configuring the DHCP assignment table in the subsection above. The "tx" message type is visible in the ASCII dump, followed on the next line by the start of my transaction 01 It also assumes that the network takes time to adjust to big price increases like we've seen in recent days. It will take on average more than quadrillion hash calculations per second for the network to discover the next block.
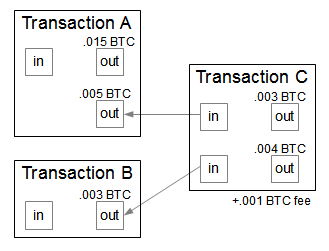
I had many questions regarding blockchain protocol and bitcoin. Generation transaction. Each output value, as well as the total, must be within the allowed range of values less than 21m coins, more than 0. Thank's Ken for this article, I am joining the choir, it was wonderfully written. Ten minutes later my script received an inv message with a new block see Wireshark trace below. Anyone who has the public key, the message, and the signature can do some simple elliptic curve arithmetic to verify that the signature is valid. I am getting proper addresses now. Thus, the pool miners share the effort to mine a block and then share in the rewards. The number of signature operations contained in the transaction is less than the signature operation limit. There are basically three ways this could happen.
