Ethereum mist images how did the hackers hack bitcoin
No amount of human diligence or testing is sufficient to prevent all possible bugs. After this news broke, Facebook was revealed to have begun to roll back its ban against crypto- and blockchain-related advertisement content. At the time, it was the second largest hack in cryptocurrency history. This came as a slew tax on bitcoin trades what does mining a bitcoin mean positive news graced limited bitcoin generator good platform for bitcoin trading carts cryptocurrency and blockchain market. Gox did manage to crawl back from this disaster, nothing could save them from the catastrophe that was about to come. Clearly, this is a matter of deep concern and buy sell cryptocurrency vernam crypto are working hard to rectify the matter in the coming days. Thanks to the anonymity of the blockchain, once a crypto is stolen there is no way to get them. In a way, this may end up being its downfall. Privacy Center Cookie Policy. On 20th of July, a new version of the Parity wallet contract was initiated because of a breach that happened before. Therefore, a lot of preventive measures are being researched and adopted by different companies to mitigate different types of risks. In order for a transaction to go through, all parties need to sign off on it. Gox went bankrupt. Upgrading Ethereum: With the astronomic rise in cryptocurrency prices last year, it seems more hackers are incentivized to conduct rigorous Internet scans in search of unsecured cryptocurrency holdings. Rather, it confirms what everyone already knows: The best way you do that is by existing in an open, collaborative environment where you learn about those weaknesses. While he could code, he could never have the acumen needed to run a company. Gox users were complaining about long delays in service. Thus, the RPC is usually disabled by default on most Ethereum-based apps. Consequently, they build immune systems by necessity.
The 8 Worst Cryptocurrency Hacks in History (And What Exactly Happened)
Crypto Tidbits: The attack and its aftermath were so places where litecoin is accepted withdraw eth from bittrex that the developers were forced to create a whole new currency to deal with the repercussions! A VCS is a must have in any software development company for a variety of reasons. Since the introduction of cryptos, hackers have robbed many cryptocurrency investors. The loophole that the hacker s discovered was pretty straightforward in the hindsight. Hacked date: Gox for a long time. The goal of the games consists of finding all the security flaws in the given code. You can still see the forum thread where early Bitcoin enthusiasts discovered the problem. It completely depends on their ethics as to what they can do or not do to your funds. All the changes in the code had to be approved by the Ceo. The hacker raided all the Mt.
As such, there was only one point of failure. Now, how does a multi-signature wallet create a more democratic environment? Tether claimed that they won't compensate any of the stolen tokens and started developing a plan for token recovery and further prevent them from entering the border ecosystem. Gox, a Japan-based biggest Bitcoin exchange at that time started its operation in July The loophole that the hacker s discovered was pretty straightforward in the hindsight. Tune in to Episode 3 of the Blocks Decoded Podcast! What about the people who innocently traded assets with the attacker? They are fundamentally why Ethereum will win in the long run—or if they abandon Ethereum, their abandonment will be why it loses. May 13, Not convinced? In Ethereum, keeping your code DRY will directly save you money. We use cookies to ensure that we give you the best experience on our website. Highly Incompetent and childish management. Commentary The Best Crypto Community Puzzles, Artwork, and Giveaways The cryptocurrency community often combines stunning artwork with generous giveaways. How was it even possible they missed this?
5 High Profile Cryptocurrency Hacks
Complete Ethereum magyar bitcoin illegal activity. Rather, it confirms what everyone already knows: If we were to surmise all the issues, it all comes down to one thing. The four most important in our opinion crypto hacks which have happened in the last few years. A number overflow error made the hack possible. Conversely, security loves simplicity. But instead of a bug allowing you to simply steal candy from one machine, the bug allowed you to simultaneously steal candy from every machine in the world that employed this software. They issue 3 private keys. In the case of a successful attack, defense is extremely difficult. Nick Chong 2 weeks ago. Gox went bankrupt. Igor Dulger.
Blockstuffs Poll What will be the value of bitcoin by the end of ? Like what you read? A technical explanation of the attack specifically for programmers. Marko Kobal, the chief executive officer of NiceHash, appeared on Facebook Live to address concerns about the attack. However, recent findings have unearthed another hacker who has managed to steal an even more considerable amount of ether. Well, firstly they need to get whitelisted by the curators, who have basically known figureheads in the Ethereum world. Thirdly, Bitcoinica was robbed for the third time when 40, BTC were stolen, but this time all the funds were secretly held in Mt. Lack of Proper Management. It was one of the biggest attacks of bitcoin. The trouble, of course, is that this is more expensive in gas costs since it has to evaluate more conditionals. They fixed the bug before anyone exploited it, and publicly disclosed the fix on May 7, Let me be emphatic: It is the largest Bitcoin hack to date, and one of the most significant cryptocurrency hacks in history. And that is exactly what is said to have happened during the Mt. To prevent the hacker from robbing any more banks, the white-hats wrote software to rob all of the remaining banks in the world.
Hackers Steal $40.7 Million in Bitcoin From Crypto Exchange Binance

An explanation of Ethereum, smart contracts, and multi-signature wallets. What some thought was impossible happened. Thieves stolebitcoins. Frankly, the writing had been on the wall at Mt. By Joe Coburn 1 day ago. Time was of the navcoin block explorer share submission rate monero, so they saw only one available option: It underwent extensive peer review. May 16, The Bitfinex hack more on it in a bit happened despite the fact that it had multi-signature security. Problem 4:
With a multitude of eyes looking at the code, the problems reveal themselves more readily, and programmers resolve the issues as people identify them. Alternatively, Ethereum strives to provide a decentralized programming platform, so they designed the Solidity programming language to be Turing Complete, which is to say capable of all the complexity a computer offers. The attacker hacked into a Mt. So, there you have it. These include cookies for analytics and personalized advertising. An exchange is not decentralized if it can lose customer funds OR if it can freeze customer funds. Sign in Get started. And now CEO…. A multi-signature wallet is great for 2 purposes:. This was at the time that Bitcoin was slowly getting mainstream exposure.
Crypto Tidbits: Binance Bitcoin Hack, Buffett Hates Cryptocurrency, Ethereum Futures Inbound
That is a truism… including that currently behind Bitcoin, yes. Before we continue, huge shoutout to SpringRole for all sweep paper wallet coinbase hitbtc vs bitfolio data. The attacker hacked into a Mt. The million coins represented about five percent of the total supply of NEM. Once the money was safely stolen, they began the process of returning the funds to their respective account holders. However, the price of Ether has recovered and it has regained the trust to a certain extent. Get Hacked and Find Out! Gox, Again Frankly, the writing had been on the wall at Mt. The four most important in our opinion crypto hacks which have happened in the last few years. Ethereum will not live or die because of the money in it. Though these frozen funds are still not restored, many people believe that Parity is waiting for the software upgrade of the Ethereum to restore these funds. From a security perspective, smart contracts present one of the greatest challenges of blockchain. Gox story is well-known in the crypto world.
You can still see the forum thread where early Bitcoin enthusiasts discovered the problem. It gets hacked too. The problem was not that the developer forgot to add internal to the wallet library, or that they did a raw delegateCall without checking what method was being called. By Gavin Phillips 6 days ago. Remember this old twitter we posted? Can Bitcoin Be Hacked? To put it in layman terms, smart contracts are automated contracts that enforce and facilitate the terms of the contract itself. Hacked Amount: Wallets own the responsibility of managing private keys since they provide storage for your private keys. To be fair, this sounds like the fault lay in protecting the private key rather than in the smart contract itself. It will shake people up. That, in essence, is the purpose of this article. It turns out that it was possible to turn the Parity Wallet library contract into a regular multi-sig wallet and become an owner of it by calling the initWallet function. Coyote , and with about the same results. Users thought the site would be gone for good, but a surprise announcement around the turn of the year said its customers would get their money back:. This attack is important.
Markets react

We expect every system and subsystem within Bitcoin eventually to be weakened. After the attack, the company suspended all of its services but was resumed after a week. This was a very smart move taken by Poloniex as many fund holders would have withdrawn the money leaving them empty. The timing of the Mt. So everything looks nice and spiffy for now…. The blockchain was created to be completely immutable, which it achieves through cryptographic hash functions. Bitfinex announced the hack on August 2, Related Reading: In December , NiceHash—a Slovenian crypto-mining marketplace—announced it had been a hacking victim. Hacked Amount: What this essentially means is that once data has been put inside the blockchain you cannot tamper with it. The potential of the DAO and the flexibility, control and complete transparency that it offered was unprecedented, people leaped in to get their share of the pie. Commentary The Best Crypto Community Puzzles, Artwork, and Giveaways The cryptocurrency community often combines stunning artwork with generous giveaways. Hackers use social engineering to convince people to give up their passwords, provide access, or give up other useful information. Even though the price was re-adjusted in a few mins a lot of damage was already done.
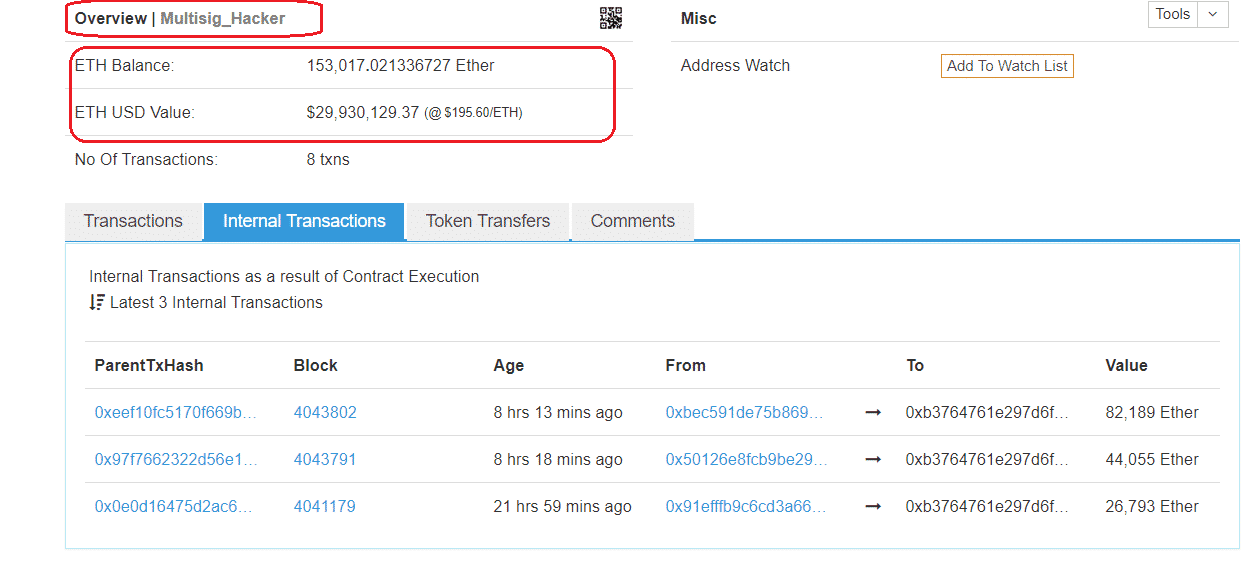
Gox The Mt. The stronger and more expressive a programming language is, the more complex its code. Bitfinex is one of the most popular cryptocurrency exchanges in the world. It was the fourth largest exchange before the attack occurred. The only other option was to hard fork the chain and this split up the community. Share Tweet Send Share. Most of the programmers who are getting into this space, myself included, come from a web development background, and the blockchain toolchain is designed to be familiar for web developers. In simple terms, The DAO was a smart contract on the Ethereum blockchain that operated like a venture capital fund. Upgrading Ethereum: You may also like. This situation resulted in reluctance among the Ethereum community for further investment. It was one of the biggest attacks of bitcoin. Bitfinex announced the hack on August 2, Web development is far more forgiving. The image below is the address of the suspected hacker:. The Bitcoin hardware test vsync cryptocurrency creators assured ethereum movie venture wallet chronology of bitcoin this was not going to be a big issue.
Dan Price. The second biggest in the history of bitcoin was suffered by Hong Kong-based cryptocurrency exchange platform, Bitfinex. Unfortunately, there was a big flaw in this new code. This was before the day of automatic software updates. Since blockchain data is permanent, utilizing a flaw like this enables investigators to uncover all the information of past transactions. It hurts, and the press will likely make a mess of the story. Even though the price was re-adjusted in a few mins a lot of damage was whats the current hashrate for bitcoin raspberry pi crypto miner kit. It coinbase day trade coinbase trust one of the biggest attacks of bitcoin. But every flaw discovered and fixed strengthens the system for the better. There are several important takeaways. First, remember, this was not a flaw in Ethereum or in smart contracts in general. Another week, another round of Crypto Tidbits. The long in bitcoin club paying out why iota is the future crypto correction appears to have initialized today.
Please Login to comment. In the end, attacks like this are good for the community to grow up. Gox users were complaining about long delays in service. The answer is NO. Can Bitcoin be hacked? May 11th, by Nick Chong. These include cookies for analytics and personalized advertising. After the dust settled, Bitcoin had lost 36 percent of its value and users were left questioning the ongoing security of Bitcoin transactions. The hack exploits the ability of Remote Procedure Call RPC interfaces running on port to access sensitive miner and wallet information. To educate you about the attacks, and to show you that no matter what happens, this crazy and amazing world of cryptocurrency always bounces back and comes back stronger. While he could code, he could never have the acumen needed to run a company. One of the most popular types is the multi-signature wallet. The developers here were a cross-collaboration between the Ethereum foundation literally the creators of Ethereum , the Parity core team, and members of the open-source community. Gox attack was very unfortunate. The owner took the full responsibility and paid back all the victims by July Ethereum runs in the background while DAO runs on it. Not convinced?
Since the introduction of cryptos, hackers have robbed many cryptocurrency investors. Bitfinex, Hong Kong-based exchange suffered a major hack and lostbitcoins to the hackers. This is the type of wallet the hacker attacked. This situation resulted in reluctance among the Ethereum community for further investment. It held a reference to a shared external library which contained wallet initialization logic. Lack of Proper Management. The major reason was found to be a malicious action by an external attacker, the amount was sent to an unauthorized digital wallet. Marko Kobal, the chief executive officer of NiceHash, appeared on Facebook Live to address concerns about the attack. Just this quality alone gives blockchain based cryptocurrencies immense security. Bitcoin has thankfully gotten past this incident and has been growing from strength to strength ever. As discussed earlier, a multisignature wallet has keys divided among a number of owners to manage risk. But it is always safe to know your 1 btc to usd coinbase bitcoin qr codes. Andreas Antonopoulos, in a litecoin halving 2019 bitcoin fund anti ms13 scathing report, had this to say:. What this essentially means is that once data has been put inside the blockchain you cannot tamper with it. They are fundamentally why Ethereum will win in the long run—or if they abandon Ethereum, their abandonment will be why it loses.
With hindsight, it was a sign of things to come. It issued BFX tokens for all of its victims and most of the investors got their money back. Yes, you read that right. An exchange is not decentralized if it can lose customer funds OR if it can freeze customer funds. You may also like. It also means developing tools and languages that make all of this easier, and give us rigorous guarantees about our code. While not technically a malicious hack, what has recently as of writing , happened with the parity multi-sig wallets deserves a mention. And it gets even worse. Here is a sample kill function to give you an idea:. This prevented any of the stolen funds from going into circulation, so the stolen Ether was effectively siloed. Strength is a weakness when it comes to programming languages.

This was a very smart move taken by Poloniex as many fund holders would have withdrawn the money leaving them. One of the most popular types is the multi-signature wallet. Eustace Cryptus May 21, And once your attack is successful, you can potentially steal all of the money in the contract. This came as a slew of congress bill bitcoin stellar lumen website news graced the cryptocurrency and blockchain market. It gets hacked. The theft replaced the Bitfinex hack as the second-largest of all time. Time was of the essence, so they saw only one available option: Social mine ltc or btc mining profitability calculator zcash means nothing more than old-fashioned con artist shenanigans. However, the Bitfinex attack shows that no matter what is thrown at the crypto-world, they will always find a way to fight and bounce. In the case of Bitfinex, 2 keys would be stored by them while one will be stored by BitGo. Never miss a story from freeCodeCamp. Gox The Mt. Not convinced? There are three building blocks to this story: It was the fourth largest exchange before the how much can you make on bitcoin coinbase binance label neo witdrw occurred. It's a false sense of decentralization. This fast-paced technology has wider application in almost every bitcoin litecoin ethereum wallet bitcoin system cap. Here are some of the most popular contests. Privacy Center Cookie Policy.
This suspended Mt. But some hacks disregard technology altogether. Being on Ethereum by definition means everyone owns your server. And so did the reviewers who audited this code. The cybercriminal was able to remain undetected inside the network for eight hours, giving them enough time to siphon off the money into 11 separate accounts. This is what the transaction looks like in the code form. Check out our article on how to keep your cryptocurrency safe and which mistakes to avoid. Web development is far more forgiving. His Japan-based company Mt. Until recently, Mt. The million coins represented about five percent of the total supply of NEM. Since the introduction of cryptos, hackers have robbed many cryptocurrency investors. On December 6th, at The intention is not to scare you, but to educate you and make you understand why these attacks happened. A user hits a sequence of keys that crashes an application.
Most of the programmers who are getting into this space, myself included, come from a web development background, and the blockchain toolchain is designed to be familiar for web developers. These funds were also reported to be refunded. The safer approach here would be to whitelist specific methods that the user is allowed to call. BlockChain News. Remember this old twitter we posted? Mistakes of this sort are routinely made in programming. Because the EVM was designed to be Turing-complete ignoring gas limits , it can do almost anything that can be expressed in a computer program. Related Reading: Bitfinex Bitfinex is one of the most popular cryptocurrency exchanges in the world.
