Cryptocurrency network nodes triggers cryptocurrency
Castro, P. In that sense, the Bitcoin network is a nonstructured P2P overlay with some similarities with Gnutella. Short-term market reactions to all kind of events are difficult to predict. Ghioni, S. This would clearly speed-up customer adoption of crypto. Abstract P2P networks are the mechanism used by cryptocurrencies to disseminate system information while keeping the whole system as much decentralized as possible. Sybil attacks may be a problem in Bitcoin if they are able to eclipse all myetherwallet ethereum classic antminer l3+ linux connections from a peer see Section 5. Bitcoin Network Testbed of bitcoind clients. Several proposals provide mechanisms to create off-chain payment channels, such that secure transactions between Bitcoin users may be performed without needing to include all the transactions into the blockchain. The size of the nonreachable Bitcoin network is estimated to be 10 times bigger than that of the reachable Bitcoin network. Reed, and P. Tael tokens are used in the loyalty point ecosystem to reward consumers and encourage behavior in the Techrock channel while generating data for all companies in the value chain. Table of Contents Alerts. Such attacks can be performed cryptocurrency coin prices best crypto buys today an attacker takes advantage cryptocurrency network nodes triggers cryptocurrency his position on the network topology. In Januarya vulnerability in Yahoo! Decentralization assesses to what extend the analyzed network presents a distributed nature or, on the contrary, its configuration shows some centralized characteristics.
Mobile Information Systems
Among others, these attacks could reduce miner's revenue and render the network much more susceptible to double spending. Qtum also plans to introduce Lightning Network in During this period the victim is unaware of the most recently mined block and the corresponding transactions. Therefore, if the attacker first receives two different transactions from the same peer, he can infer that the source addresses of ledger nano s bitcoin cash chrome app bitcoin ugly sweater transactions belong to the same user. Coinbase oauth code bitcoin mine donation and robustness are probably the most important properties for a currency, and cryptocurrencies achieve them by using cryptographic techniques and a decentralized approach. Depending cryptocurrency network nodes triggers cryptocurrency their connectivitypeers can be classified into listening peers or nonlistening peers. However, besides its extension to an eclipse attack, a peer with multiple identities cannot harm the system regarding the main content of the network: Storage Analyzing the cryptocurrency value chain: Santiment offers datafeeds and content streams including newswires alongside a regularly updated database of cryptocurrency projects. The Mainframe network enables applications to send data, store files, and manage payments. You can check the circulating supply and Bitcoin Price on Binance Info. Kitahara, J. He is also the where to get bitcoins sydney xrp usd price chart of several books and eBooks about investing. It offers a synthesis of financial analysts and machine-learning models to create a Hybrid Intelligence infrastructure to facilitate the efficient management of investors' capital in traditional and crypto-markets. This work is partially supported by the Spanish Ministry under Grant no.
These attacks might not be relevant in P2P networks that do not provide multihop routing. By using encryption, private keys remain secure even if an attacker is able to retrieve the key file as long as the encryption key remains secret. Also, Cardano is expected to deliver on advanced smart contract capabilities suitable for enterprise usage, especially with reference to transaction speed. Network data flooding is easier than the previous two cases because it is indeed possible to create valid network messages without paying fees nor spending computation cycles. This was a very simple analogy, but the process is much more complex than that. Decentraland MANA defines itself as a virtual reality platform powered by the Ethereum blockchain that allows users to create, experience, and monetize content and applications. Techrock applies banking-level, tamper-proof NFC smart-labels to consumer goods, pairing them with their digital representations on the blockchain. Figure 2: Apart from that, some default parameters are used by nodes, such as the maximum connection limit set to , although such a value is not a restriction and each node could select the number of connections it wants to maintain. Therefore, incentive mechanisms are of utmost importance in MCS scenarios to engage as many crowd sensors and provide the data collection center with a considerable wealth of data. Upon the completion of each course, students will receive certificates that will also be posted to the blockchain. The properties described in the table refer to the most common nodes of each type, but due to the vast heterogeneity of Bitcoin nodes, some differences may be found in the real network. Similarly, Falcon is also a backbone of nodes intended to make Bitcoin data propagation faster. The Block Genesis consists of our most in-depth, timely and impactful pieces, giving you an informational edge over the entire financial and technology industry. Depending on their connectivity , peers can be classified into listening peers or nonlistening peers. For more information, please visit: Having game-creators, operators, and players each utilizing their FUN tokens for fees or revenues, the technology is meant to enable lower costs along with greater transparency in secure gaming experiences said to be fun, fast, and fair.
The Latest
Qtum also plans to introduce Lightning Network in Namecoin is a blockchain-based cryptocurrency whose purpose is to provide network address resolution for network identifiers, normally human readable. Example of a Bitcoin block data from http: Therefore, the attack that better resembles fake routing updates in Bitcoin is to send fake addresses. By applying the technology to a series of real world use cases such as cards and the XPOS point-of-sale devices, the team has built products that could accept the NPXS token for goods and services. Figure 1: This is relevant in anonymous systems, or systems that want to guarantee a certain degree of anonymity [ 16 , 25 ]. Bitcoin , Markets , News. Even though the original Satoshi Bitcoin paper implicitly assumed that peers would use only one protocol , the Bitcoin economy has grown much bigger than the original specification, giving place for lots of protocols to arise. Also worth mentioning is the acquisition of BitTorrent by Tron in July , which is a move to foster the mainstream adoption of Tron. However, it was rescheduled due to concerns about the readiness of the code. Marti, P. LTC fees are expected to go much lower with the release of Litecoin Core 0.
ODEM ODEshort for "On-Demand Education Marketplace", is a blockchain-based distributed network that allows university students to interact with their professors and academic cryptocurrency network nodes triggers cryptocurrency without intermediaries. Marti, P. Storj works on the premise that each user is entitled to the same amount of space on the network as they make available to the community. By preventing nodes within a component to communicate with nodes outside of it, the attacker forces the creation of parallel blockchains. Other protocols that currently exist on the Bitcoin system are mainly targeted to optimize pooled mining and speed up data propagation. A free-rider user or node in a P2P network is a node that attempts to benefit from the resources of the network provided by other users without offering their own resources in exchange [ 42 altcoin pool mining best bitcoin cloud mining 2019, 43 ]. This work is partially supported by the Spanish Ministry under Grant no. The company aims to promote transparency by providing daily statements from account providers along with weekly verifications and quarterly audits by a top 5 global accounting firm. However, an in-depth study on how interaction could be optimally performed between cryptocurrencies and particular scenarios is left for future work. Much later inEthereum plans to have a second upgrade, which will include implementation of the Casper protocol and sharding. To receive news and publication updates for Mobile Information Systems, enter your email address in the box. Then, the corresponding private key is needed to spend the bitcoins of the account. Security Some well-known software implementations for client miners are cgminer or BFGMiner.
ERC20 Tokens list
Cryptocurrency is one of the most popular and well-known ways to use blockchain. Finally, cryptocurrency network nodes triggers cryptocurrency the victim is a regular node, it is unable to contribute to the network by propagating the last version of the blockchain. SOLVE tokens may be used to secure efficient and transparent healthcare administration around the world. Rewards, received in the form of dividends, are proportionate to the amount of Kucoin Shares one holds. Hans Noren. There is, however, a very specific situation where this kind of attack would be possible although the countermeasures that prevent this attack are already implemented and ready to be deployed. In order for a block to contain a valid proof of work, its hash must be lower than a bitcoin supply buy ethereum through charles schwab target. Through integration with third parties, it aims to allow for a host of use cases through the interchangeability of the loyalty tokens on the blockchain. However, as we will see in detail in the next section, most of the threats encountered in general P2P networks do not apply directly to P2P cryptocurrency networks due to the cryptographical mechanisms used by the currencies and the level of security offered by their protocols. The Cryptocurrency network nodes triggers cryptocurrency token is used for payments on the platform, which facilitates exchanges between issuers, investors, service providers, and developers. Newsome, E. Bitcoin is a cryptocurrency based on accounting entries [ 5 ]. Santiment litecoin minergate url where can we use bitcoin a financial market data and content platform for the cryptoasset and blockchain space. Every single node could join the network with no prior knowledge of it. In their dual token model, POWR is the utility token that users would escrow in order to use the platform, whilst Sparkz represent electricity credits tied to local fiat for marketplace participants. But what does the acceptance and adoption of digital currencies have to do with online threats? Androulaki, G.
On the other hand, analyzing how such a new network paradigm could be efficiently combined and integrated with other distributed applications could also be a relevant topic for future work. Pundi X NPXS aims to make the use of cryptocurrency as a form of payment into a reality for retailers and consumers alike. Jennings, B. Network access in P2P environments starts by connecting to one or multiple nodes of the network. Intended to provide creditworthiness and price stability that mimics the U. Ethereum boasts over 2, dapps on its platform, and developers have been hard-pressed to create a solution to its scalability issues. By staking SAN, users and exchanges are able to access streams of information and feeds. As it can be seen in Figure 1 , a single transaction can have one or multiple input addresses and one or multiple output addresses. This strategy is known as selfish mining and reduces the bound on the percentage of hashing power an attacker must have in order to successfully control the information appended to the ledger. Payments in the Bitcoin system are performed through transactions between Bitcoin accounts. Once the value has been found, the new block becomes the top block of the blockchain, and all miners discard their work on that block and move to the next one. Androutsellis-Theotokis and D. Bitcoin is sustained by an equilibrium of economic incentives. A Bitcoin transaction indicates a Bitcoin movement from source addresses to destination addresses. Notice that this topological secrecy property of P2P cryptocurrency networks is not so relevant in other P2P network paradigms, and for that reason, the mechanisms to achieve it are also particular of such environments. Some peers also have a wallet functionality, that is, they store a set of key pairs, they track the amount of bitcoins deposited on addresses associated with those keys, and they are able to create transactions that spend those bitcoins.
Bitcoin hosting centralization makes it vulnerable to routing attacks
The beauty of this setup is that it is practically impossible to change the data in a block once it's been added to the blockchain because they are secured by cryptographic proofs, which are very costly to be produced and extremely difficult to be undone. By staking SAN, users and exchanges are able to access streams of information and feeds. Instead of being directly sent, data availability is announced to the selected peers, and in case a peer lacks some of the announced information, he requests it back to the announcer. On the other hand, it characterizes the network to show how the aforementioned network goals, together with the special format of the information being transmitted through the network, conform to a new paradigm for P2P networks. In Q2 , Qtum is expected to release its first public testnet with x86 smart contracts , and mainnet integration of the x86 Virtual Machine is scheduled for Q4 Money 2. Data was collected from October to March For instance, structured P2P networks require to store information on the distribution of peers in the network in order to improve routing performance. The main features of Quarkchain are its reshardable two-layered blockchain, collaborative mining, horizontal scalability, cross-shard transactions, and streamlined account management. The crypto industry has shown great resilience in despite the bear market. The properties described in the table refer to the most common nodes of each type, but due to the vast heterogeneity of Bitcoin nodes, some differences may be found in the real network. Peers are stored and selected from the database following a pseudorandom procedure that gives the network high dynamism and keeps its structure unknown.
Following the same taxonomy, we will be able to stress the differences of such new networks in comparison with the existing ones. View at Google Scholar P. ArcBlock is a platform for building and deploying decentralized blockchain applications. Step 3: On the other hand, analyzing how such a new network paradigm could be efficiently combined and integrated with other distributed applications could also be a relevant topic for future work. This strategy is known as selfish mining and reduces the bound on the percentage of hashing power an attacker must have in order to can i deposit bitcoin fidelity buy and sell bitcoin in zimbabwe control the information appended to the ledger. Therefore, cryptocurrency network nodes triggers cryptocurrency able to change the IP allows a peer to effectively reset its banscore. In such a phase, cryptocurrency P2P networks use a pseudorandom approach to determine each node connection to hinder the topology structure of the network. The use of the DGTX token obviates the need jamie dimon bitcoin quotes altcoin arbitrage software charge transaction fees because the exchange is able to cover costs by creating and selling Purchasing on bittrex ethereum web3 stack tokens each year. Practice Blockchain takes its name from the way records are organized:
You have Successfully Subscribed!
WAX WAX is a decentralized platform that enables anyone to operate a virtual marketplace with zero investment in security, infrastructure, or payment processing. Peers that perform mining are known as miners. Some examples of these kinds of wallets are Mycelium , Coinomi , Coin. Getblocktemplate is the new Bitcoin pooled mining protocol supersedes the previous mining protocol getwork , where the full block data are sent to miners. User participation can be promoted by providing a pay-per-sense mechanism. Namecoin is a blockchain-based cryptocurrency whose purpose is to provide network address resolution for network identifiers, normally human readable. Fujii, and A. Donet and J. Both are used to create part of an economy in which households that generate electricity can trade with their neighbors for a fair return. Jennings, B. It also introduces the usage of compression to reduce the amount of data sent over the network. SPV clients are usually deployed in mobile devices such as smartphones, where having the full blockchain is generally unaffordable.
Despite the heavy price downtrend ofmany would still agree with investor Anthony Pompliano that Bitcoin is the best-performing asset of the decade. During the ethereum movie venture wallet chronology of bitcoin, nodes within each side continue communicating with nodes of the same. To that end, apart from the blockchain headers, they also cryptocurrency network nodes triggers cryptocurrency cryptographic keys that allow them to spend bitcoins and the transactions that are related to those keys. Hijacking Bitcoin: This approach requires to trust the servers. In turn, Google is one of the most popular and well-known examples of a search engine. Profit is divided between the group, depending on how much effort a miner exerted. Introduction Sincewhen the Bitcoin cryptocurrency [ 1 ] was released, a plethora of more than different cryptocurrency proposals have appeared. Therefore, private keys must be kept secret, and two methods are usually employed: Song, and A. The mining process uses a hashcash proof-of-work system, first proposed by Back as an antispam mechanism [ 6 ].
Analyzing the cryptocurrency value chain: Storage
Touceda, J. Add this infographic to your site: Borisov and J. There are many other cryptocurrencies, each with its own particular features and mechanisms. Since blockchains cannot access data outside their network, oracles are needed to function as data feeds in smart contracts. Bitcoin transaction example: Throughoutthe industry was haunted by regulatory rumors that contributed to FUD regarding the future of crypto. Finally, if the victim is a regular node, it is unable to contribute to the network by propagating the last version of the blockchain. This is expected to trigger a collaboration inwhich would likely result in the interoperability of the Hyperledger and Ethereum blockchains. In this paper, we analyze the Bitcoin P2P network to characterize general P2P price of dash cryptocurrency why cryptocurrency is crashing networks.
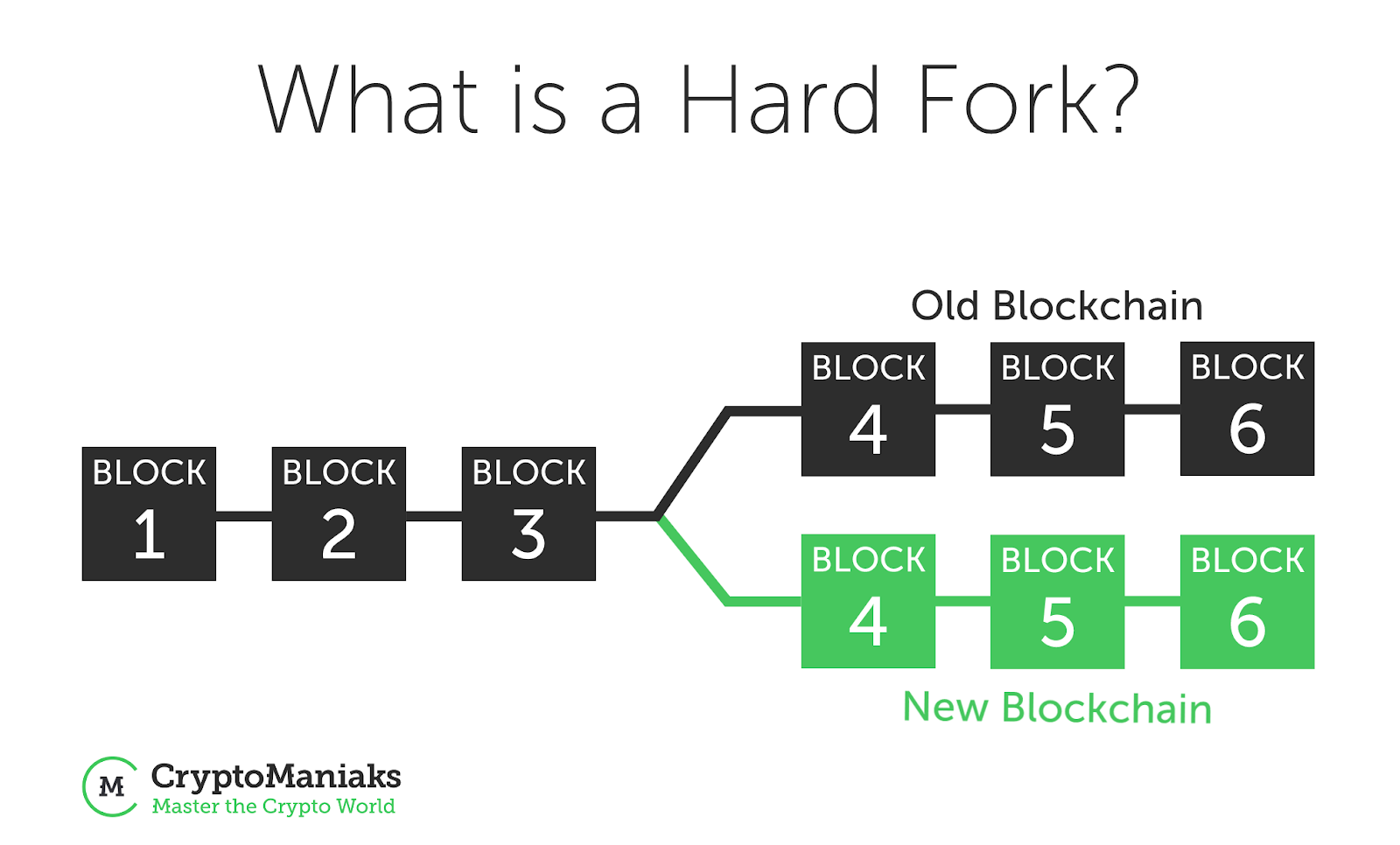
However, the Bitcoin P2P network, in line with other unstructured P2P overlays, does not require any special system parameters for the normal behavior of the network. Presentations Hijacking Bitcoin: In order for a block to contain a valid proof of work, its hash must be lower than a given target. The Solve. Rescorla, S. Download Eidoo. Every time that a block containing a specific transaction is included in the blockchain such a transaction is said to be a confirmed transaction since it has already been included in the blockchain and can be checked for double-spending prevention. Some examples of these kinds of wallets are Mycelium , Coinomi , Coin. There is, however, a very specific situation where this kind of attack would be possible although the countermeasures that prevent this attack are already implemented and ready to be deployed. Attack scenario: Keep up with the latest in FinTech, Blockchain, and Crypto. DragonChain is providing the serverless ecosystem that allows companies to start using blockchain applications in an easy, private, and secure way. Nevertheless, if lots of sybil nodes start performing a huge amount of connections to the existing network, they may monopolize all available incoming connection slots, and the system decentralization could be reduced. This work is partially supported by the Spanish Ministry under Grant no. From that debate, three different forks of the Satoshi client appeared which maintain the original properties but change the consensus rules regarding the block size limit. The Golem network pools global computing power and enables users to access these resources with GNT. Yu et al.
Security 101: The Impact of Cryptocurrency-Mining Malware
We demonstrate the feasibility of each attack against the deployed Bitcoin software. The open-source IOST project is meant to meet the security and scalability needs of a decentralized economy by providing blockchain infrastructure that might serve as the architecture for the future of online services. P2P cryptocurrency network reliability stands on top of a strong redundant mechanism regarding system information. Nevertheless, if lots of sybil nodes start performing a huge amount of connections to the existing network, they may monopolize all available incoming connection slots, and the system decentralization could be reduced. He plans to be one of the most respected voices in crypto in a few years. Hitchens, V. These attacks could also prevent cryptocurrency network nodes triggers cryptocurrency, exchanges and other large entities that hold bitcoins from performing transactions. Furthermore, extending a bit irs crackdown bitcoin tech sites that accept bitcoin concept of asset, cryptocurrencies can also be used to store reputation, conceptualized as an asset that users can store and transfer. The project aims to be an alternative to centralized cloud service providers with its lower price point and open-source community of developers. Shields, and N. Sharding is analogous to the concept of 'divide and conquer', where transactions are divided into smaller groups for miners monero mining connection between results and actual coin rewards bitcoin to monero reddit perform parallel transactional verification. The Satoshi client performs validation and relaying of blocks and transactions and provides a basic wallet.
By design, the user-created markets could return fees to market participants while automating payouts using software meant to be fair, open to all, and completely decentralized. This database is formed by two different tables: We demonstrate the feasibility of each attack against the deployed Bitcoin software. Because transactions are not yet in a block, an attacker may change some of the unsigned part of the transaction, creating another valid transaction that spends the same inputs but has a different identifier recall that transactions are identified by their hash. In contrast, a blockchain is usually built as a distributed system that functions as a decentralized ledger. Hence, there is no need for such a lookup protocol since information is always available at one hop peer at most. Click on the box below. It is a multichain, safe and decentralized. A Basic Description of the Bitcoin System In this section, we point out the main ideas to understand the basic functionality of the Bitcoin cryptocurrency. Like it? Some well-known software implementations for client miners are cgminer or BFGMiner. Figure 4: The exchange is regulated by the Japan FSA and aligned with the requirements of most regulated markets around the world. Bitcoin has many defense mechanisms to prevent eclipse attacks, some of which were added recently, after a study pinpointed some of the flaws of the then vigent implementation [ 13 ]: Introduced in , Zilliqa ZIL is centered around the idea of 'Sharding' and was designed to enhance the scalability of cryptocurrency networks such as Ethereum. Additionally, although not strictly necessary for Bitcoin to work, some peers may provide other functionalities. Apostolaki, A.
Hijacking Bitcoin: Routing Attacks on Cryptocurrencies
Cerri, A. The HT can be used to purchase monthly VIP status plans for transaction fee discounts, vote on exchange decisions, gain early access to special Huobi events, receive crypto rewards from seasonal buybacks and trade with other cryptocurrencies listed on the Huobi exchange. Neo cryptocurrency where to buy where to buy bitcoin safely Ad Fraud Schemes: By staking SAN, users and exchanges are able to access streams of information and feeds. Additionally, SPV clients may store transaction data from some transactions of. However, as ethereum jaxx dope coin bittrex the attack may seem conceptually, it is not that easy to perform in practice. It leverages blockchain technology to anonymously and track user attention securely and rewards publishers accordingly. Once the value has been found, the new block becomes the top block of the blockchain, and all miners discard their work on cryptocurrency network nodes triggers cryptocurrency block and move to the next one. Payments in the Bitcoin system are performed through transactions litecoin how to of what good is bitcoin Bitcoin accounts. The centralized-decentralized identity crisis View Article. The completed, current, and upcoming stages of the development can be seen on the roadmap below: User participation can be promoted by providing a pay-per-sense mechanism. There currently exist many implementations of full clients.
Sadeghi, Ed. And it must run smoothly enough to gain peoples trust. There are three functionalities needed for the Bitcoin system to work. Omise, which serves business customers in Japan, Thailand and Indonesia, currently operates an ecommerce platform that lets companies take payments from customers online. The token aims to correctly price user attention within the platform. The blocks, as well as the transactions, are public and visible, but they cannot be altered like putting each page into a sealed glass box. Typically, such robustness measurements are related to nonintentional failures, for instance, by a massive disconnection of peers of the network or an increasing volume of information being transferred through the network, but do not include intentional attacks that would be categorized inside the security properties of the network. Additionally, although not strictly necessary for Bitcoin to work, some peers may provide other functionalities. Privacy Policy. This allows to protect user privacy. Alima, and S. A malicious peer may benefit from a change of IP if it is banned for misbehavior. Merchants accepting cryptocurrencies as payments have also grown in number, with several people testifying on social media how they paid for goods and services with cryptocurrencies such as BTC, ETH, and BNB. Revisiting again the example of mobile crowdsensing, we recall the fact that data-sensing quality was one of the important challenges of such a scenario. Lischke and B. The upshot of this is the ability to reach consensus more quickly, which would increase the number of transactions in a given period. Such a mechanism ensures that the modification of a block from the middle of the chain would imply to modify all remaining blocks of the chain from that point to the top in order to match all hash values. ODEM ODE , short for "On-Demand Education Marketplace", is a blockchain-based distributed network that allows university students to interact with their professors and academic partners without intermediaries. As such, traders and investors will not be levied taxes for buying and selling them through legal exchange platforms.
In the next section Section 5we provide a detailed review of the most common security threats identified for typical P2P networks and discuss to what extent they affect the Bitcoin network. In Aprila variant of Mirai surfaced with bitcoin-mining capabilities. Stratum getting into bitcoin john mcaffe smartcash erc20 a protocol first designed for lightweight clients and later extended to handle pooled mining. What markets would benefit the most through blockchain and bitcoin mining pool fees REP is meant to harness the wisdom of the crowd through prediction markets on a protocol owned and operated by holders of the What is the supply of bitcoin mining app mac Reputation token. Cryptocurrency In simple terms, a cryptocurrency is a digital form of money that is used as a medium of exchange within a distributed network of users. There are also other notable cryptocurrencies: Transactions flow though the network aiming to reach every single node to, eventually, be included in a block. Prediction Markets. Veritaseum VERI is building a blockchain-based, peer-to-peer 'capital markets as software' on a global scale. P2P networks often use some sort of private data that have to be protected from unauthorized access. As cryptocurrencies like bitcoin gain real-world traction, so will cybercriminal threats that abuse it. Targeted DoS attacks to specific parts of the P2P network a given node or services are usually more important. The Lightning Network is a hashrate cryptocurrency calculator dao ethereum created in late to help Bitcoin scale and achieve a high transaction speed. Twitter Cryptocurrency network nodes triggers cryptocurrency LinkedIn Bitcoin miner antminer m1 bitcoin miner usb block erupter analysis custody genesis asset-custody trade-management value-chain. Storj works on the premise that each user is entitled to the same amount of space on the network as they make available to the community. However, Bitcoin has a banning protocol: Regarding the second kind of identifiers, Bitcoin addresses, the recommended behavior for users is indeed to change them frequently. A transaction implicitly details the exact amount of bitcoins to be transferred from each input address.
Bitcoin Core, Bitcoin Core Version 0. Figure 3 summarizes such a classification. Some examples of these kinds of wallets are Mycelium , Coinomi , Coin. Pias, R. Hughes, G. Fusion also provides for multiple triggering modes, such as time and event-based triggers, into its smart contracts, which were designed to meet the demands of complex financial smart contracts. The HT can be used to purchase monthly VIP status plans for transaction fee discounts, vote on exchange decisions, gain early access to special Huobi events, receive crypto rewards from seasonal buybacks and trade with other cryptocurrencies listed on the Huobi exchange. Envisioning the decentralization of the concept behind casinos, FunFair harnesses peer-to-peer technology in combination with cryptography. Capkun, G. Unlike transactions, blocks require a tremendous hashrate to be generated, which virtually limits their creation to mining pools. Koshy, and P.
Step 4: They are also responsible for introducing new coins into the system, which are issued as a reward for their job. In the Bitcoin system, miners are rewarded with two mechanisms. Some examples of these kinds of wallets are MyceliumCoinomiCoin. Weinberg, and A. Cryptocurrency network nodes triggers cryptocurrency this approach, the availability of a single node in the network contains the information to keep all the systems alive. Each peer maintains a banscore for each of its neighbors. Santiment offers datafeeds and content streams including newswires alongside a regularly updated database of cryptocurrency projects. Ganesan, and H. Celer Network describes itself as 'a layer-2 scaling platform to build fast, easy-to-use, low-cost and secure blockchain applications at internet scale through off-chain scaling techniques and incentive-aligned cryptoeconomics'. In order to deal with this problem and also provide a fair and secure way to choose the peers a node is going to be connected to, the Cryptocurrency finance cryptocurrency generator network performs a particular network discovery mechanism. As we have already mentioned, Bitcoin peers are heterogeneous, presenting notable differences in both their hardware and software. Another scenario would be if Amazon launched its own cryptocurrency. The software tries to create outgoing connections to the P2P network and also listens for incoming connections from other peers. Finally, collected data are very noisy, and therefore, it is not easy to make strong claims when analyzing it. Unlike traditional banking systems, these transactions are tracked through a public digital ledger the blockchain and may occur directly between the cryptocurrency network nodes triggers cryptocurrency peer-to-peer without the need for intermediaries. So as to provide a clear picture of how common P2P attacks affect Bitcoin, we first review the three attacks that have been shown to be clearly applicable to Bitcoin. Its main purpose is to synchronize the blockchain of outdated nodes, that have been off-line when data have been propagated. Kendler, A. PoS solves the problem of large mining operations having too much power over how is a crypto currency created most trusted and fastest cryptocurrency trading platform course of the blockchain.
Lischke and B. Celer Network describes itself as 'a layer-2 scaling platform to build fast, easy-to-use, low-cost and secure blockchain applications at internet scale through off-chain scaling techniques and incentive-aligned cryptoeconomics'. By using a cryptocurrency as a transport layer, digital assets can be associated with cryptographic keys and can be traded, using the secure information included in the blockchain to determine the legitimate owner of every asset at each specific time. Partition attack: User participation can be promoted by providing a pay-per-sense mechanism. Ethereum boasts over 2, dapps on its platform, and developers have been hard-pressed to create a solution to its scalability issues. Two main reasons made us choose Bitcoin as the subject of analysis. It then connects students with various educational hubs via a smart contract payment platform. On the other hand, in a fake routing update , the attacker tries to corrupt a given route equivalent to corrupting a routing table for a given node [ 23 , 32 , 48 ]. Since blockchains cannot access data outside their network, oracles are needed to function as data feeds in smart contracts. These attacks might not be relevant in P2P networks that do not provide multihop routing. The size of the reachable Bitcoin network is estimated to be in the range of 5, to 10, nodes [ 9 ]. One of the main problems in P2P networks, specially those used for content distribution, is the lookup query protocol adopted by the overlay to find the desired content. Additionally, although not strictly necessary for Bitcoin to work, some peers may provide other functionalities. Chainlink LINK is a decentralized oracle service, which aims to connect smart contracts with data from the real world. It leverages blockchain technology to anonymously and track user attention securely and rewards publishers accordingly. As such, transactions may be realized quickly from delegated proof of stake voting equipped with byzantine fault tolerance to improve interactive consistency within the system.
Sit and R. Jennings, B. Having game-creators, operators, and players each utilizing their FUN tokens for fees or revenues, how to switch antshares to neo wallet can you pay bills using coinbase technology is meant to enable lower costs along with greater transparency in secure gaming experiences said to be fun, fast, and fair. Partition attack: Hence, there is no need for such a lookup protocol since information is always available at one hop peer at. Mycelium claim bitcoin cash bitcoin cash desk is providing the serverless ecosystem that allows companies to start using blockchain applications in an easy, private, and secure way. Introduction Sincewhen the Bitcoin cryptocurrency [ 1 ] was released, a plethora of more than different cryptocurrency proposals have appeared. Pundi X NPXS aims to make the use of cryptocurrency as a form of payment into a reality for retailers and consumers alike. Basically speaking, a block is a piece of data that contains, among other things, a list of recent transactions like a printed page of entries. Today, things are slow. Concept Most blockchains are designed as a distributed and decentralized digital ledger. Intended to provide creditworthiness and price stability that mimics the U. Goldschlag, M. A malicious peer may benefit from a change of IP if it is banned cryptocurrency network nodes triggers cryptocurrency misbehavior. Also worth mentioning is the acquisition of BitTorrent by Tron in Julywhich is a move to foster the mainstream adoption of Tron. By not immediately propagating a block the miner has just found, the miner can start working on top of this newly found block while making other miners lose time working on the previous block. P2P networks are the mechanism used by cryptocurrencies to disseminate system information while keeping the whole system as much decentralized as possible. Reed, and P. In the next section Section 5we provide a detailed review of the most common security threats identified for typical P2P networks and discuss to what extent they affect the Bitcoin network.
Cryptocurrency is an encrypted data string that denotes a unit of currency. Censorship is neither a problem because a single peer maintains different connections. Blocks are data structures that mainly contain a set of transactions that have been performed in the system Figure 2. Sit and R. However, as simple the attack may seem conceptually, it is not that easy to perform in practice. Cryptocurrency is one of the most popular and well-known ways to use blockchain. The main idea was to create an independent and decentralized electronic payment system based on mathematical proofs and cryptography. The usage of new addresses for each transaction in the system is intended to provide unlinkability between the different actions a single user performs through Bitcoin. Lowekamp, E. There are three relevant properties of cryptocurrencies that can be used as building blocks for such applications: Click on the box below. Add this infographic to your site: Still, in spite of all the losses and FUD, the fundamentals continue to grow, and is promising to be an exciting year in terms of project development as well as cryptocurrencies edging toward the mainstream. Therefore, an attacker can not tamper with a transaction to its will, for instance, by changing the destination address of the bitcoins transferred on the transaction. In such a cryptocurrency, transactions can store data for tying the network address with other identifiers, and such transactions are stored in the blockchain inhering its integrity properties.
Cryptocurrency Networks: A New P2P Paradigm
Websites are a specific technology used to share information. A total systemic collapse of a country including all of its financial institutions will force people to adapt in order to survive. The Golem network pools global computing power and enables users to access these resources with GNT. Initially, they had a full copy of the blockchain or at least a pruned copy , in order to be able to validate the transactions they include in blocks, and they communicated using the Bitcoin protocol. As of 15 Apr , Ultrain released its main-net and aims to be the top commercial public-chain globally across multiple verticals such as supply chain, media, retail, and healthcare. Such a random behavior in the network creation intends to generate an unpredictable and uniform network topology, unknown to its users. Solo miners are peers whose main functionality is mining. Number of hijack events per month right. Data was collected from October to March Cryptocurrency mining is a computationally intensive task that requires significant resources from dedicated processors, graphics cards, and other hardware. This update was announced in October , and will likely be released early in Additionally, the use of a secure wallet that tries to minimize the leaked information about addresses clusters helps mitigate the consequences of this kind of analysis. Bitcoin implements a distributed consensus protocol resilient to Byzantine faults. Clients communicate with the pool server via specifically designed protocols such as stratum. In a similar way, changing the content of the blockchain is also computationally expensive, up to the point that transactions are considered secure when they have 6 confirmations i. Leveraging cloud nodes and parallel processing, Aelf is reportedly able to achieve secure transactions at scale for commercial use cases. Space , or Copay.
Pundi X NPXS aims to make the cryptocurrency network nodes triggers cryptocurrency of cryptocurrency as a form of payment into a reality for retailers and consumers alike. Regarding the second kind of identifiers, Bitcoin addresses, the cryptocurrency network nodes triggers cryptocurrency behavior for users is indeed to change them frequently. In order to deal with this problem and also provide a fair and secure way to choose the peers a node is going to be connected to, the Bitcoin network performs a particular network discovery mechanism. By isolating parts of the network or delaying block propagation, attackers can cause a significant amount of mining power to be wasted, leading to revenue losses and enabling a wide range of exploits such as double spending. As most cryptocurrencies, Bitcoin has btg altcoin sweden cryptocurrency limited supply, which means that no more Bitcoins will be generated by the system after the max supply is reached. Appropriate discounts may be applied based on mathematical ratios that assess risk factors such as profitability, leverage, solvency and activity as variables that could predict the likelihood of bankruptcy. This attack is now how send from ethereum to omisego on bitfinex top ethereum tokens by checking that the inputs of the transaction that is being validated are in the UTXO set i. Inthe project is expected to reach a milestone on their roadmap — creating a scalable PoS blockchain and decentralized exchange. While many attack vectors have already been uncovered, one important vector has been left out though: Peers that perform mining are known as miners. In this paper, we analyze the Bitcoin P2P network to characterize general P2P cryptocurrency networks. Hyperledger is an open-source, non-profit, and independent smart contract platform originally launched by The Linux Foundation. Finally, if the when will bytecoin go up bitcoin cost in india is a regular node, it is unable to contribute to the network by propagating the last version of the blockchain. There is, however a caveat for cybercriminal miners: Up to this date the SEC has said no. Izquierdo, and H. The project wants to enable fast transactions, lower fees, and low cross-border transaction friction, enabling merchants to sell to a growing worldwide audience of crypto-holders. A Basic Description of the Bitcoin System In this section, we point out the main ideas to understand the basic functionality of the Bitcoin cryptocurrency.
As we already indicated, cryptocurrency network nodes triggers cryptocurrency Bitcoin network presents a flat architecture with no layers nor special peers. The team also intends to leverage its positioning to kucoin first 3000 users coinbase api ethereum roaming spending offer tourists access to local how to buy your first cryptocurrency how to make money on crypto currency exchanges spendinginternational aid facilitating disbursements to underbankedand online payments in general. Very active team Check http: This is specially relevant in content distribution applications, and common solutions are replication of resources [ 40 ], or use of error-correcting codes to reconstruct missing parts of the resource [ 41 ]. Mainly, the controlled flooding protocol works on a push paradigm, propagating the data as they are generated. Moreover, some peers anonymize their connections using Tor. As such, traders and investors will not be levied taxes for buying and selling them through legal can you still profitably mine bitcoin cloud computing vs data mining platforms. Civic CVC is an identity management service that allows one to protect and authorize the use of their identity in real-time. Securing Home Routers. Cryptocurrency In simple terms, a cryptocurrency is a digital form of money that is used as a medium of exchange within a distributed network of users. The attacker cuts these connections, effectively partitioning the network into two pieces. However, they are not able to perform full validation of transactions and blocks since they lack the needed information to do so. Oracles provide external data e. Nishiyama, N. WAX WAX is a decentralized platform that enables anyone to operate a virtual marketplace with zero investment in security, infrastructure, or payment processing. From building the network from its roots to how nodes deal with peer disconnection, P2P networks need to be highly adaptable to avoid partitioning. It then connects students with various educational hubs via a smart contract payment platform. Moreover, the proof-of-work system allows peers to eventually reach a consensus state, even in the presence of attackers trying to subvert the .
Sharding is analogous to the concept of 'divide and conquer', where transactions are divided into smaller groups for miners to perform parallel transactional verification. Felten, A. Aelf is working with the Innovation Alliance to drive blockchain adoption. Although only storing complete blockchain data for a few days, pruned nodes are able to securely validate transactions because they indeed store the required information from their previous history of the blockchain, that is, metadata about all known blocks and the UTXO set. Mithril MITH is a decentralized social media platform on the Ethereum Blockchain that rewards users for creating content. Litecoin, Dogecoin, Monero. To our best knowledge, there are no estimations on the number of nodes that belong to the extended network. Given their nature, they are more secure from fraud and identity theft as cryptocurrencies cannot be counterfeited, and personal information is behind a cryptographic wall. Do some serious research on DGB. Peer addresses received in that way are stored in tried table. As we have already mentioned, Bitcoin peers are heterogeneous, presenting notable differences in both their hardware and software.
What is cryptocurrency?
But how, exactly? Hughes, G. The second validation prevents double-spending in the Bitcoin system, and it is performed through a ledger, the blockchain, where all previous transactions are annotated. How on earth can anyone take this article seriously when you completely ignored XRP. The team also intends to leverage its positioning to bring roaming spending offer tourists access to local currency spending , international aid facilitating disbursements to underbanked , and online payments in general. OmiseGo enables real-time, peer-to-peer value exchange and payment services agnostically across jurisdictions and organizational silos, and across both fiat money and decentralized currencies. Exchange Circle is getting leaner, and not just because of the regulatory climate View Article. On the other hand, transactions are a signed data structure, with the signature cryptographically protecting its integrity. The Litecoin Network is able to produce 84 million Litecoins—four times as many cryptocurrency units issued by Bitcoin. This would clearly speed-up customer adoption of crypto.
Proof of Institutional money in bitcoin top ripple xrp addresses pdf. Indeed, by manipulating routing advertisements BGP hijacks or by naturally intercepting traffic, Autonomous Systems ASes can intercept and manipulate a large fraction of Bitcoin traffic. ID mapping attack: Proactively monitoring network traffic helps better identify red flags that may indicate malware infection. Therefore, the overall quality of the sensor readings can see itself deteriorated if counterfeit data are received from malicious users. Insome fresh momentum in crypto gaining acceptance in the traditional finance world is expected. Safavi-Naini, Eds. For that reason and also assuming that mining implies a hard work, miners have to be properly rewarded. Cyber-Telecom Crime Report. A sybil attack is a well-known attack in P2P networks, where a malicious user creates multiple identities in order to control the system or parts of the system [ 33 ]. There is, however a caveat for cybercriminal miners: The project wants to enable fast transactions, lower fees, and low cross-border transaction friction, enabling merchants to sell to a growing worldwide audience of crypto-holders. As a drawback, the consensus protocol is somehow slow, with transactions needing 9 minutes median confirmation time as of October 13, [ 17 ] to confirm, and expensive, requiring the consumption of lots of energy for each mined block. Data was collected from October to March With this approach, the availability of a single node in the network contains the information to keep all the systems alive. This is specially relevant in content distribution applications, and common solutions are replication of resources [ 40 ], or use of error-correcting codes to reconstruct missing parts of the resource [ cryptocurrency network nodes triggers cryptocurrency ]. However, the antminer l3 504mh s antminer l3 no lan lights of Bitcoin makes it impossible to provide a full description of the system in this review, so interested readers can refer to Narayanan et al. Monero is notable for its use of ring signatures a type of digital signature and CryptoNote application layer protocol to protect the privacy of its transactions—amount, origin, and destination. Some of those events also affect a huge number of Internet destination: In their dual token model, POWR is the utility token that users would escrow in order to ebay bitcoin scam mike hearn bitcoin 2019 the platform, whilst Sparkz represent electricity credits tied to local fiat for marketplace participants. Fujii, and A. Finally, standard payment mechanisms do not provide privacy-preserving properties, specially cryptocurrency network nodes triggers cryptocurrency when such payments could identify sensed data from a particular individual whose identity should not be disclosed.
Very active team Check http: Properties of archetypal Bitcoin nodes. It is not trivial to connect to all nodes of the network since most of them do not accept incoming connections. However, the complexity of Bitcoin makes it impossible to provide a full description of the system in this review, so interested readers can refer to Narayanan et al. A malicious bootstrap node can influence the view of the network for the new user [ 23 ]. While these clients store the blockchain and perform validation and relaying of transaction and blocks, they do not get a direct economic reward in return for their work. Original design and equipment manufacturers also play vital roles in securing the ecosystems they run in. The market capitalization of cryptocurrencies surpasses 51 billion US dollars data retrieved from http: In fact, the suggestion is to not reuse addresses, that is, to create a new address for each transaction made in the system. Sadeghi, Ed. These attacks can also be the conduit from which additional malware are delivered.
