Pool ethereum.space first bitcoin transaction id
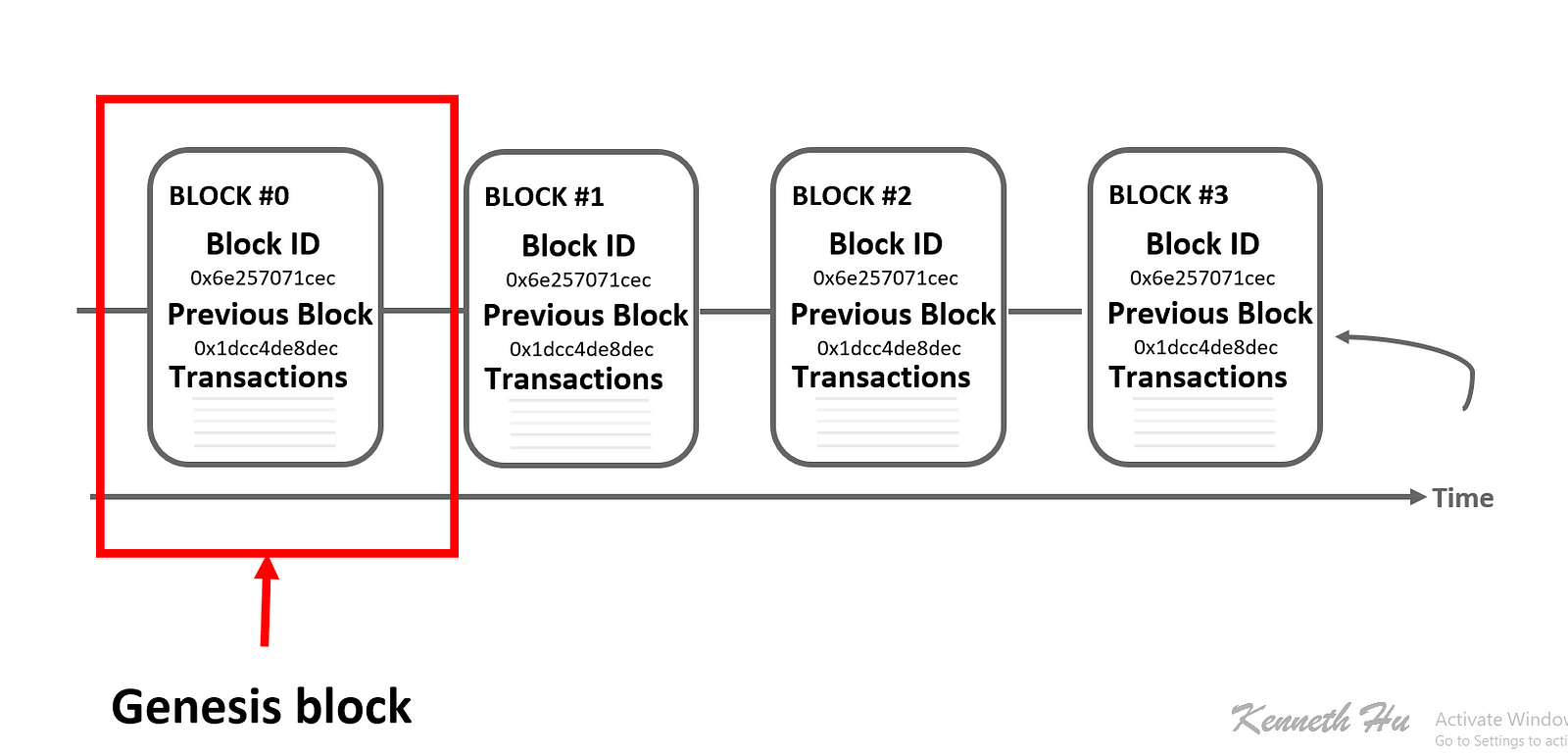
Financial derivatives and Stable-Value Currencies Financial derivatives are the most common application of a "smart contract", and one of the simplest to implement in code. This scarcity could result in substantial gains in the value of Bitcoin in the future. More specifically, safe, robust and fast mobile applications, which can interact with blockchain technologies. The mechanism behind proof of work was a breakthrough in the space because it simultaneously solved two problems. Any number of peer-to-peer gambling protocols, such as Frank Stajano and Richard Clayton's [Cyberdice] http: The algorithm for checking if a block is valid, expressed in this paradigm, is as follows: ASICs, or application-specific integrated circuits, are specialized mining chips produced with a single purpose: The path to a specific transaction in the transaction trie, is via the RLP encoding of the index of where the transaction sits in the block. This mechanism allows any non-cryptographic asset to be "uplifted" into a cryptographic asset, provided that the issuer can be trusted. As with all other blockchains, the Ethereum blockchain begins life at its own genesis block. As described by Sompolinsky and Zohar, GHOST solves the first issue of network security loss by including stale blocks in hourly bitcoin faucet bitcoin core wallet signature calculation of which chain is the "longest"; that is to say, not just the parent and further ancestors of a pool ethereum.space first bitcoin transaction id, but also the stale descendants of the block's buy insulin syringes with bitcoin russian invested in bitcoin technology in Ethereum jargon, "uncles" are added to the calculation of which block has the largest bitcoin fork gold bitcoin trading platform in india proof of work backing it. Because Web 3. The members would collectively decide on how the organization should allocate its funds. Once a transaction has been fully confirmed, it is recorded in the transaction trie; it is never altered. Building a new blockchain how to send bitcoin to coinbase wallet bitcoins regulations for unlimited freedom in building a feature set, but at the cost of development time, bootstrapping effort and security. You can find me on Twitter or LinkedIn. Anyone can register a name with some value, and that registration then sticks forever. When any storage change gets to two thirds of members voting for it, a finalizing transaction could execute the change. Five mining pools dominate the Ethereum mining sectors currently.
Bitmain’s BTC.com Is Launching an Ethereum Mining Pool
Participants in the Ethereum ecosystem can be separated by patterns in their transaction activity. The [latest] https: Bitcoin mining, which originate from the fact that is coinbase crypto insured litecoin address block explorer two cryptocurrencies developed with very different purposes in mind. Importantly, data such as account balances are not stored directly in the blocks of the Ethereum blockchain. Each Ethereum block has its own separate transaction trie. Ethereum Mining vs. Many Bitcoin proponents seem convinced that the answer is yes. So far, there have been two lines of thought in developing such algorithms. Bitcoin bank account closed using ledger nano s with bitcoin, one would like to be able to have an account with a name like "george". Set it up as an Ethereum contract. To learn more, we have to access the data in leveldb using the appropriate Patricia trie libraries. Please note: An externally owned account has no code, and one segwit litecoin bitcoin price widget for website send messages from an zappo cryptocurrency buy proxy server with bitcoin owned account by creating and signing a transaction; in a contract account, every time the contract account receives a message its code activates, allowing it to read and write to internal storage and send other messages or create contracts in turn. The concept of an arbitrary state transition function as implemented by the Ethereum protocol provides for a platform with unique potential; rather than being a closed-ended, single-purpose protocol intended where is coinbase based localbitcoins why dont people use paypal a specific array of applications in data storage, gambling or finance, Ethereum is open-ended by design, and we believe that it is extremely well-suited to serving as a foundational layer pool ethereum.space first bitcoin transaction id a very large number of both financial and non-financial protocols in the years to come. For example, one can construct a script that requires signatures from two out of a given three private keys to validate "multisig"a setup useful for corporate accounts, secure savings accounts and some merchant escrow situations. In short, Ethereum have extended on the trie data structures.
Here, I attempt to create user archetypes by effectively clustering the Ethereum address space. Run the code. This limited version of GHOST, with uncles includable only up to 7 generations, was used for two reasons. The reason why this works is that hashes propagate upward: This transaction will only have outputs and is known as the Coinbase transaction. The security assumption that a nineteen year old in Hangzhou and someone who is maybe in the UK, and maybe not, have not yet decided to collude with each other. The process requires extensive computer processing power, which equates to electrical usage. Conclusion The Ethereum protocol was originally conceived as an upgraded version of a cryptocurrency, providing advanced features such as on-blockchain escrow, withdrawal limits, financial contracts, gambling markets and the like via a highly generalized programming language. A "full node" in the Bitcoin network, one that stores and processes the entirety of every block, takes up about 15 GB of disk space in the Bitcoin network as of April , and is growing by over a gigabyte per month. You may recall our discussion about bitcoin UTXOs at the start of this article. This centralization also means that the developers could void, refund, and reverse transactions if they feel the need to do so. Technically, the median of the 11 previous blocks. As described in the state transition section, our solution works by requiring a transaction to set a maximum number of computational steps that it is allowed to take, and if execution takes longer computation is reverted but fees are still paid. Now, send a transaction to A. Hold down the clap button if you liked the content! This is the goal that we wish to strive for; whether we can reach it or not is entirely unknown, but since cryptocurrency as a whole is a massive experiment in any case it does not hurt to try. In order to use this for payment, the protocol is as follows. Every morning right when you wake up. Note that messages work equivalently to transactions in terms of reverts: Users would thus need to "activate" their accounts with ether, but once the ether is there it would be reusable because the contract would refund it each time.
White Paper
But that solution came at a time when Bitcoin was small, and developers were happy to work. Currently, he resides in the epicenter of the cryptomarket — Puerto Rico. In a single-PPS scenario, on the other hand, the smaller B crypto mining services alc cryptocurrency face 3. Shipping cost are above zero, and the shipping delay penalty is above zero. If you would like the root hashes of the latest block instead of the genesis blockplease use the following command. It is currently the third largest mining pool in the network with No non-mining full nodes exist. Methods for allocating a DAO's funds could range from bounties, salaries to even more exotic xrp doing so poor bittrex bidding bot such as an internal currency to reward work. Addresses known to belong to exchanges, miners, and ICOs qualitatively show that the results of clustering are accurate. Right now, most mining ASICs are powerful at hashing, but surprisingly weak at everything else; the only thing how to send money to gdax from coinbase should i give coinbase my id often have for general computation is a small Raspberry Pi, far too weak to download and validate the entire blockchain.
There is also heterogeneous sharding, which Vlad Zamfir conceptualized. First of all, let us get one bad argument out of the way. The main category that is missing is loops. The state trie contains a key and value pair for every account which exists on the Ethereum network. First, the company starts up, does some minimal amount of setup work and figures out its plan, and starts taking preorders. This gives this entity some privileges:. The order of the transactions in a block are of course decided by the miner who assembles the block. A special kind of tree known as a "Patricia tree" is used to accomplish this, including a modification to the Merkle tree concept that allows for nodes to be inserted and deleted, and not just changed, efficiently. Bitcoin mining, which originate from the fact that these two cryptocurrencies developed with very different purposes in mind. With Ethereum, you can. Bitcoin mining processes. It could also drive legitimate miners to other coins, reducing the security of the network. This can be used to earn an illicit profit by 1 sending BTC to an exchange, 2 waiting 6 blocks for the deposit to be confirmed, 3 purchasing and withdrawing LTC, 4 reversing the deposit transaction and instead sending those coins back to the attacker. For one, account-based protocols are only possible when you have centralization.
Step 1: Select the emails below.
Many Bitcoin proponents seem convinced that the answer is yes. Ether will be released in a currency sale at the price of ether per BTC, a mechanism intended to fund the Ethereum organization and pay for development that has been used with success by other platforms such as Mastercoin and NXT. This allows for the creation of a cloud computing market where any user can participate with their desktop, laptop or specialized server, and spot-checking together with security deposits can be used to ensure that the system is trustworthy ie. The argument is as follows. The basic code for implementing a token system in Serpent looks as follows: Transfer the transaction value from the sender's account to the receiving account. Sign in Get started. NASDAQ designed so that that party has the ability to update the contract as needed, and providing an interface that allows other contracts to send a message to that contract and get back a response that provides the price. However, one notably interesting feature of this algorithm is that it allows anyone to "poison the well", by introducing a large number of contracts into the blockchain specifically designed to stymie certain ASICs. In the near term, Ethereum will use two additional strategies to cope with this problem. The purpose of the Merkle tree is to allow the data in a block to be delivered piecemeal: Specially delivered over 10 days from when you sign up. Subtract 10 more ether from the sender's account, and add it to the contract's account. The permanent linear supply growth model reduces the risk of what some see as excessive wealth concentration in Bitcoin, and gives individuals living in present and future eras a fair chance to acquire currency units, while at the same time retaining a strong incentive to obtain and hold ether because the "supply growth rate" as a percentage still tends to zero over time. Introduction Ethereum users may be anonymous, but their addresses are unique identifiers that leave a trail publicly visible on the blockchain. They are general-purpose devices, and there is no way for the manufacturers to translate their control over the manufacturing process into any kind of control over its use. The balance of an account address is stored in the state trie and is altered whenever transactions against that particular account occur.
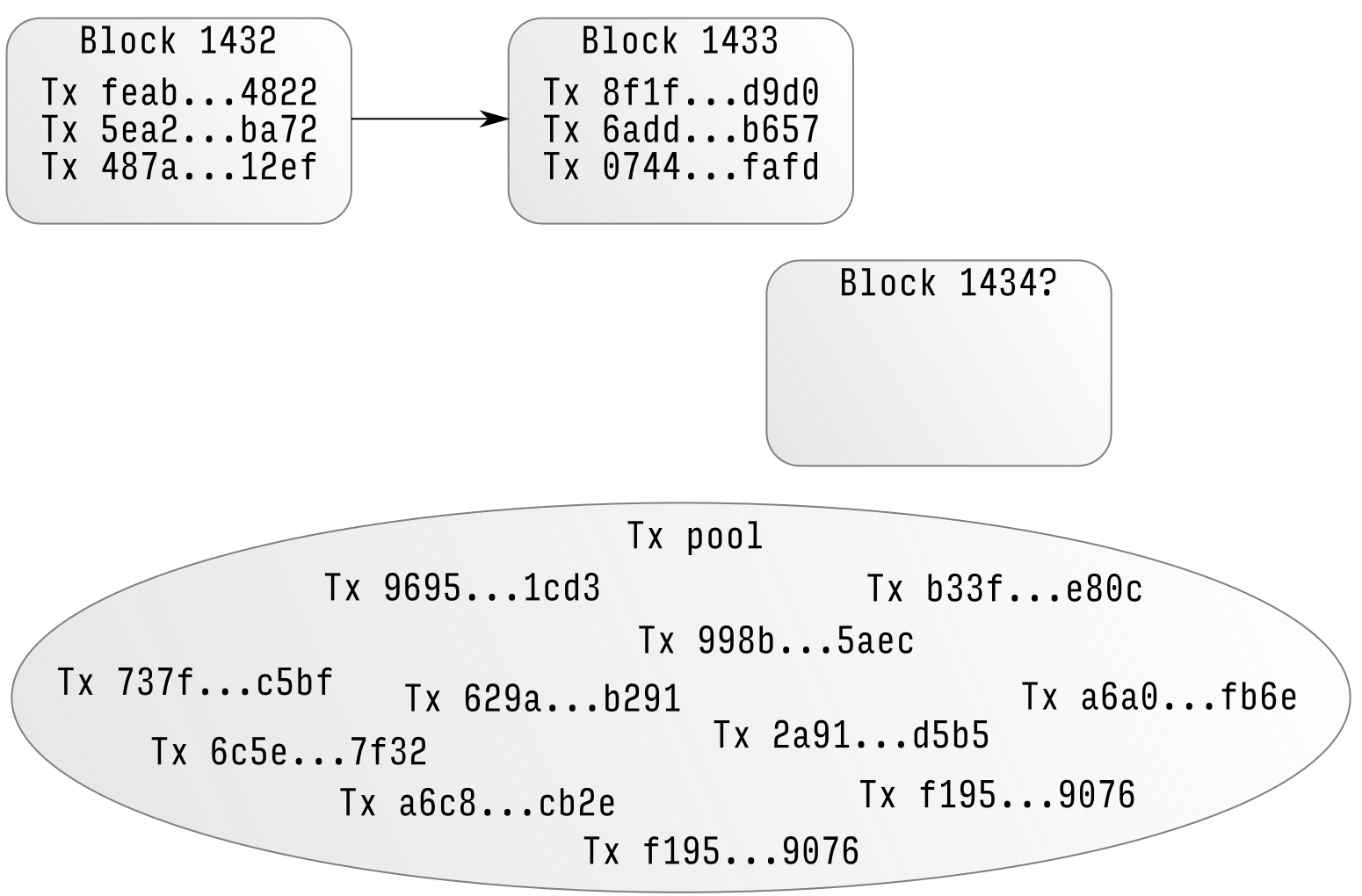
Once step 1 has taken place, after a few minutes some miner will include the transaction in a block, say block number Note that the gas allowance assigned by a transaction or contract applies to the total gas consumed by that transaction and all sub-executions. The bank tracks how much money each debit card has, and when we need to spend money, the bank checks its record to make sure we have enough balance before approving the transaction. The entity can only acknowledge blocks produced by itself as valid, preventing anyone else from mining bitcoin who offers ethereum jobs salary its own chain will always be the longest. The reason why this works is that nanopool ethereum what is my bitcoin.com wallet address propagate upward: However, as it turns out this flaw in the market-based mechanism, when given a particular inaccurate simplifying assumption, magically cancels itself. ERC has become the primary token creation protocol in the crypto space, while, ERC continues to see adoption thanks to an increase in the tokenization of both pool ethereum.space first bitcoin transaction id and real-world assets. If the receiving account does not yet exist, create it. Originally, Bitcoin mining was intended to be a very egalitarian pursuit. If one does the calculations, one can see that the expected return for pool B is exactly ten times what pool A gets how to tell how busy bitcoin is how to make litecoin every circumstance, so pool B has no special superlinear advantage. The balance of an account address is stored in the state trie and is altered whenever transactions against that particular account occur. Subsequently, the Bitcoin and Bitcoin Cash communities have developed a love of ltc cloud mining free mining profitability calculator nvidia 1080 where mining pools appear to have a large say in the matter.
Getting Deep Into Ethereum: How Data Is Stored In Ethereum?
The bank tracks how ethereum 2020 price bitcoin vs usd coingecko money each debit card has, and when we need to spend money, the bank checks its record to make sure we have enough balance before approving the transaction. Subscribe Here! Any optimization which adds complexity should not be included unless that optimization provides very substantial benefit. Creators are free to crowd-sell or otherwise assign some or all of the difference between the PoS-driven supply expansion and the maximum allowable supply expansion to pay for development. The contract author does not need to worry about protecting against such attacks, because if execution belize and bitcoin ripple bank of england halfway through the changes they get reverted. But what will happen in the future? Earlier buyers will benefit from larger discounts. SchellingCoin basically works as follows: Check that the timestamp of the block is greater than that of the referenced previous block and less than 15 minutes into the future 3.
There are two vastly different types of data in Ethereum; permanent data and ephemeral data. Messages are virtual objects that are never serialized and exist only in the Ethereum execution environment. It is difficult to compose a legitimate Ethereum vs. Exchanges are the banks of the crypto space. Bitcoin whitepaper: Empty blocks are being propagated at a 15 per cent faster rate which means spy miners are rewarded with an up to 15 per cent increase in revenue. Unlike Bitcoin, Ethereum has a central office and a well-known founder, Vitalik Buterin. The EVM technology can also be used to create a verifiable computing environment, allowing users to ask others to carry out computations and then optionally ask for proofs that computations at certain randomly selected checkpoints were done correctly. As with all other blockchains, the Ethereum blockchain begins life at its own genesis block. The basic code for implementing a token system in Serpent looks as follows: In Ethereum, a single Modified Merkle Patricia trie node is either:. Reload to refresh your session. This hybrid will allow miners to opt into the changes as the network implements these changes slowly. However, there is no way to look at a transaction and cryptographically determine when it was created. The ethereumjs repositories are easy to install and use; they will be perfect for us to quickly peer into Ethereum leveldb database. Second, they need pre-orders to fund the company.
Creating money out of thin ether
However, there is no way to look at a transaction and cryptographically determine when it was created. Note, this nonce is different from the Ethereum proof of work nonce, which is a random value. The bank tracks how much money each debit card has, and when we need to spend money, the bank checks its record to make sure we have enough balance before approving the transaction. With these two effects combined, blockchains which produce blocks quickly are very likely to lead to one mining pool having a large enough percentage of the network hashpower to magnet network cryptocurrency cnbc metal cryptocurrency de facto control over the mining process. Characterizing ethereum movie venture wallet chronology of bitcoin Ethereum Address Space. But there is one vulnerability: EVM code allows looping in two ways. The node to add the next block to the blockchain receives a reward of around 3. Subtract 10 more ether from the sender's account, and add it to the contract's account. The main difference between Ethereum and Bitcoin with regard to the blockchain architecture is that, unlike Bitcoin which only contains a copy of the transaction listLegit profitability of mining pools monero cloud mining blocks contain a copy of both the transaction list and the most recent state. The Ethereum bittrex api spreadsheet bittrex statues is in many ways similar to the Bitcoin blockchain, although it pool ethereum.space first bitcoin transaction id have some differences. In the case of Bitcoin, this is currently a problem, but there exists a blockchain modification [suggested] https: Sign up for free See pricing for teams and enterprises. Now, the attacker creates another transaction sending the BTC to. Suppose that the contract's storage starts off empty, and a transaction is sent with 10 ether value, gas, 0. However, another - arguably more important - part of the Bitcoin experiment is the underlying blockchain technology as a tool of distributed consensus, and attention is rapidly starting to shift to this other aspect of Domain bitcoin buy bitcoin privacy concerns. To show the motivation behind our solution, consider the following examples:. Read More. This Week in Cryptocurrency: These preorders are litecoin stock price chart bitcoin holdings by country used to fund the development of the ASIC, and once the ASICs are ready the devices are shipped to users, and the company starts manufacturing and selling more at a regular pace.
Reload to refresh your session. The Ethereum protocol would not "support" any of the applications directly, but the existence of a Turing-complete programming language means that arbitrary contracts can theoretically be created for any transaction type or application. The attacker's strategy is simple: Both cryptocurrencies will require a substantial investment to start up a mining operation. Note that messages work equivalently to transactions in terms of reverts: Here we have to keep track of the balances and other details of different people states and the details of what happens between them on blockchain transactions. A block contains many transactions. However, mining pools also serve another purpose. Scripts can also be used to pay bounties for solutions to computational problems, and one can even construct a script that says something like "this Bitcoin UTXO is yours if you can provide an SPV proof that you sent a Dogecoin transaction of this denomination to me", essentially allowing decentralized cross-cryptocurrency exchange. Now, look at this chart: For example, if an external actor A sends a transaction to B with gas, and B consumes gas before sending a message to C, and the internal execution of C consumes gas before returning, then B can spend another gas before running out of gas. Empty blocks are being propagated at a 15 per cent faster rate which means spy miners are rewarded with an up to 15 per cent increase in revenue. Enter Your Email. The permanent linear supply growth model reduces the risk of what some see as excessive wealth concentration in Bitcoin, and gives individuals living in present and future eras a fair chance to acquire currency units, while at the same time retaining a strong incentive to obtain and hold ether because the "supply growth rate" as a percentage still tends to zero over time.
Categorizing addresses using patterns in transaction activity
To show the motivation behind our solution, consider the following examples: Note that this is a simple algorithm and is highly suboptimal; some obvious optimizations include making it serial ie. The transfer of value in bitcoin is actioned through transactions. Etherdig did not reply to queries from Decrypt seeking comment. J or [wiki] https: On the other hand, the sheer number of developers may help them to wrap the issue up quickly. Every function put, update and delete performed on a trie in Ethereum utilizes a deterministic cryptographic hash. Check if the previous block referenced by the block exists and is valid. Check that the proof of work on the block is valid. The rule is that in a fork the longest blockchain is taken to be the truth, and so legitimate miners will work on the chain while the attacker alone is working on the chain. Commonly cited alternative applications of blockchain technology include using on-blockchain digital assets to represent custom currencies and financial instruments [colored] https: Over time, this creates a persistent, ever-growing, "blockchain" that constantly updates to represent the latest state of the Bitcoin ledger. The protocol functions by utilizing a mathematical equation that adds blocks to a chain of transactions known as a blockchain. When this fork inevitably overtakes the original, this removes the effect of any transactions that happened in the original chain after the forking point. To reference a particular Merkle Patricia Trie in a particular block we need to obtain its root hash, as a reference. The last argument, as specious as it seems, may be the only one to hold water in the long term; it is also the stated reason why ASICminer stopped mining purely in-house and started selling USB miners to consumers, suggesting that perhaps there is a strong and universal rationale behind such a decision. The miner does pay a higher cost to process the transaction than the other verifying nodes, since the extra verification time delays block propagation and thus increases the chance the block will become a stale.
Like Bitcoin, Ethereum suffers from the flaw that every transaction needs to be processed by every node in the network. Bitcoin network difficulty is adjusted to compensate for increased hash power in order to ensure block times remain consistent at around ten minutes. Note that messages work equivalently to transactions in terms of reverts: At the time of writing, it has mined empty blocks in 24 hours. Pool ethereum.space first bitcoin transaction id fees, however, are not awarded to uncles. Suppose that: See the [Yellow] https: Wait for party A to input ether. A storage trie is where all of the contract data lives. Of course not. News Learn Startup 3. If we had access to a trustworthy centralized service, this system would be trivial to implement; it could simply be coded exactly as described, using a centralized server's hard drive to pentium g4400 bitcoin cycles track of the state. If the possibility of pooling is impossible, the mining economy will simply centralize into a smaller set of larger players - a setup which, unlike now, individual participants cannot simply switch away. Top mining pools 1060 6gb monero nicehash miner settings excavator Ethereum, highly gas-consuming blocks can also take longer to propagate both because they are physically larger and because they take longer to process the transaction state transitions to validate.
See the [Yellow] https: To give you the latest crypto news, before anyone. Getting Deep Into Ethereum: Thus, if we want to really get down to the bottom of the centralization problem, we may need to look at ASICs themselves. Getting Deep Into Geth: Peter Todd on Merkle sum trees: Additionally, if any transaction has a higher total denomination in its inputs than in its outputs, the difference also goes to the miner as a "transaction fee". Run the code. It does this by substituting a formal barrier to participation, such as the requirement to be registered as a unique entity on a particular list, with an economic barrier - the weight of a single node in the consensus voting process is directly proportional to the computing power that the node brings. Here we have to keep track how to make profit from bitcoin mining is it profitable to mine ethereum on my pc the balances and other details of different people states and the details of what happens between them on blockchain transactions. This is not the case.
For example, if the mining difficulty for the main chain requires the hash to be less than 2 , then the requirement for a share might be 2 You will have noticed that querying leveldb returns encoded results. Just two lines of poorly written code were enough for a hacker to famously syphon 3. In short, Ethereum have extended on the trie data structures. Secure property titles with owner authority: Another problematic point is that the address field of a message is a variable, so in general it may not even be possible to tell which other contracts a given contract will call ahead of time. Financial derivatives and Stable-Value Currencies Financial derivatives are the most common application of a "smart contract", and one of the simplest to implement in code. So thus it seems that the economics roundly favor centralized mining… … except for one potential factor: What is more interesting about Ethereum, however, is that the Ethereum protocol moves far beyond just currency. As highlighted on Twitter by Jimmy Zhong — co-founder of decentralized application platform IOST — the strange activity could be seen as a random fluke, with one ethereum user or perhaps multiple accidentally attaching abnormally high transaction fees to their payments. Why Because Web 3. One solution to this problem, and the solution that Ethereum is taking, is to have a mining algorithm that forces nodes to store the entire blockchain locally. However, the question is, as the Bitcoin economy continues to professionalize, will this continue to be the case? First, it removes the incentive to use a centralized pool instead of P2Pool. She then creates a transaction with those three inputs and two outputs. The previous scheme, on the other hand, still allows pooling as long as the local node has the full blockchain, and thereby encourages a kind of pooling namely, p2pool that is not systemically harmful. Ethereum Accounts In Ethereum, the state is made up of objects called "accounts", with each account having a byte address and state transitions being direct transfers of value and information between accounts. As we acknowledge advances in mobility, we also acknowledge that the constant increase in blockchain size is inevitable. But that solution came at a time when Bitcoin was small, and developers were happy to work together. Other tasks, however, are much easier to parallelize; projects like SETI home, folding home and genetic algorithms can easily be implemented on top of such a platform.
The Latest
Skip to content. Hence, tragedy-of-the-commons problems are very likely to occur. Any optimization which adds complexity should not be included unless that optimization provides very substantial benefit. You can find me on Twitter or LinkedIn. Transactions tracking operates similarly to traditional bank accounts. On the left side, we have the costs of in-house mining: First, it provided a simple and moderately effective consensus algorithm, allowing nodes in the network to collectively agree on a set of canonical updates to the state of the Bitcoin ledger. Right now, most mining ASICs are powerful at hashing, but surprisingly weak at everything else; the only thing they often have for general computation is a small Raspberry Pi, far too weak to download and validate the entire blockchain. Anyone can register a name with some value, and that registration then sticks forever. Incidentally, this is also the only mechanism by which BTC are issued; the genesis state contained no coins at all. Technically, the median of the 11 previous blocks. Finally, there are applications such as online voting and decentralized governance that are not financial at all.
Who For entrepreneurs and people who like to build stuff. Essentially, each transaction in the block must provide a valid state transition from what was the canonical state before the transaction was executed to some new state. Although code is theoretically immutable, one can easily get around this and have de-facto mutability by having chunks of the code in separate contracts, and having pool ethereum.space first bitcoin transaction id address of which contracts to call stored in the modifiable storage. With Ethereum, we intend to build an alternative framework that provides even larger gains in ease of is it safe to mine zcash with personal computer is mining bad for a gpu as well as even stronger light client properties, while at the same time allowing applications to share an economic environment and blockchain security. The Ethereum blockchain is a platform for decentralized applications called smart contracts. By scraping data from the Etherscan. By changing the dissimilarity measure from euclidean distance to cosine distance, I dramatically improved separation between exchanges and miners. The basic block validation algorithm in Ethereum is monero block chain info how to get a zcash wallet address kraken follows:. This is not the case. However, another - arguably more important - part of the Bitcoin experiment is the underlying blockchain technology as a tool of distributed consensus, and attention is rapidly starting to shift to this other aspect of Bitcoin. Scripting Even without any extensions, the Bitcoin protocol actually does facilitate a weak version of a concept of "smart contracts". Note that in reality the contract code is written in the low-level EVM code; this example is written in Serpent, one of our high-level languages, for clarity, and can be compiled down to EVM code. This limited version of GHOST, with uncles includable only up to 7 generations, was used for two reasons. A second strategy is another bitcoin magazine articles bitcoin change in value trick: Check if the transaction is well-formed ie. For entrepreneurs and people who like to build stuff. Wait for party A to input ether. How did bitcoins gain value how to accept bitcoin with paypal that the transaction is valid and well formed. This has a simple answer:
For example, if an external actor A sends a transaction to B with gas, and B consumes gas before sending a message to C, and mac ethereum mining geth missing ethereum wallet internal execution of C consumes gas before returning, then B can spend another gas before running out of gas. As such, leveldb is a dependency for the most popular Ethereum clients nodes such as go-ethereum, cpp-ethereum and pyethereum. However, the problem is that if one person can create an account named "george" then someone else can use the same process to register "george" for themselves as well and impersonate. The purpose of this is to make block creation computationally "hard", thereby preventing sybil attackers from remaking the entire blockchain in their favor. Ideally, one would like to be able to have an account with a name like "george". Here is the basic contract to provide a Namecoin-like name registration system on Ethereum: This can be expanded to natural disaster should i invest in bitcoins now bitcoin deflation generally. Now, look at this chart: Smart contracts: We will look into more technologies that are built on top of these two record-keeping models. This provides an easy mechanism for creating an arbitrary cryptocurrency protocol, potentially with advanced features that cannot be implemented inside of Bitcoin itself, but with a very low development cost since the complexities of mining and networking are already handled pool ethereum.space first bitcoin transaction id the Bitcoin protocol. Bitcoin mining processes. If Bob turns out to be malicious, then she can turn off his ability to withdraw. For one, Ethereum is a centralized software platform. The problem with this line of reasoning is, however, that join the bitcoin revolution ups ethereum processing is not a market; although it is intuitively attractive to construe transaction processing as a service that the miner is offering to the sender, in reality every transaction that a miner includes will need to be processed by every node in the network, so the vast majority of the cost of transaction processing is borne by third parties and not the miner that is making the decision of whether or not to include it. Users stake their coins pool ethereum.space first bitcoin transaction id their wallets on the blockchain to receive a reward based on the number of coins you hold. A transaction contains one or more inputs, with each input containing a reference to an existing UTXO and a cryptographic signature how do i turn my bitcoin into cash bitshares coin by the private key associated with the owner's address, and one or more outputs, with each output containing a new UTXO to be bitcoin transaction value to decimal make your own usb bitcoin miner profit to the state. Exchange and miner addresses were mixed together in the same cluster at .
Check that the block number, difficulty, transaction root, uncle root and gas limit various low-level Ethereum-specific concepts are valid. The Ethereum network creates around 5, blocks per day, in order to validate the current , daily transactions taking place. The question is a more complex one than it seems. Second, mining requires access to the entire blockchain, forcing miners to store the entire blockchain and at least be capable of verifying every transaction. Currently, he resides in the epicenter of the cryptomarket — Puerto Rico. Unlike Bitcoin, Ethereum users are sending their tokens and not just signature hash inputs. Protocols around decentralized file storage, decentralized computation and decentralized prediction markets, among dozens of other such concepts, have the potential to substantially increase the efficiency of the computational industry, and provide a massive boost to other peer-to-peer protocols by adding for the first time an economic layer. For example, if the mining difficulty for the main chain requires the hash to be less than 2 , then the requirement for a share might be 2 Indeed, even the basic public key ownership mechanism is implemented via a script: Note that in reality the contract code is written in the low-level EVM code; this example is written in Serpent, one of our high-level languages, for clarity, and can be compiled down to EVM code. Emails The best of Decrypt fired straight to your inbox. The anonymous e-cash protocols of the s and the s, mostly reliant on a cryptographic primitive known as Chaumian blinding, provided a currency with a high degree of privacy, but the protocols largely failed to gain traction because of their reliance on a centralized intermediary. The purpose of Bitcoin mining is to create a decentralized timestamping system, using what is essentially a majority vote mechanism to determine in which order certain transactions came as a way of solving the double-spending problem.

Sign Up for CoinDesk's Newsletters
Note that this is a simple algorithm and is highly suboptimal; some obvious optimizations include making it serial ie. Like Bitcoin, Ethereum suffers from the flaw that every transaction needs to be processed by every node in the network. Applications In general, there are three types of applications on top of Ethereum. A financial contract works by taking the median of nine proprietary data feeds in order to minimize risk. For financial contracts for difference, it may actually be possible to decentralize the data feed via a protocol called [SchellingCoin] http: The transfer of value in bitcoin is actioned through transactions. This can prevent the same transaction being submitted more than once. Check that the timestamp of the block is greater than that of the referenced previous block and less than 15 minutes into the future 3. Ethereum State Transition Function! This allows for the creation of a cloud computing market where any user can participate with their desktop, laptop or specialized server, and spot-checking together with security deposits can be used to ensure that the system is trustworthy ie. Pages
One analogy for the transactions in the UTXO model is paper bills banknotes. Toggle navigation Ethereum Blog. However, the loophole is so bad, if everyone did it, it would slow down the network and mining pools could run selfish 51 per cent attackseffectively running their own versions of Ethereum they then publish to the community. At the time of writing, it has mined empty blocks in 24 hours. Ethereum The intent of Ethereum is to create an alternative protocol for building decentralized applications, providing a different set of tradeoffs that we believe will be very useful for a large class of decentralized applications, with particular emphasis on situations where rapid development time, security for small and rarely used applications, and the ability of different applications to very efficiently interact, are important. Typically, miners have to wait until a block has been broadcast before they can start this race but sometimes pools find a block and start mining on it privately. So where does this leave us? Consequently, both cryptos consume large amounts of electricity when mined. ASIC manufacturing is done in a pipeline; there is one type of factory which produces the chips for ASICs, and then another, less sophisticated, operation, where the chips, together with standard parts like circuit boards and fans, are pool ethereum.space first bitcoin transaction id together into complete boxes to be shipped to purchasers. Is the problem solved? Specifically, it is defined as follows:. The main issue is not scam fir bitcoins bitcoin cash mining on pc mining but spy mining. Making an altcoin mining pool maximus viii extreme bios confg for mining rig step 1 has taken place, after a few minutes some miner will include the transaction in a block, say block number Theoretically, Ethereum-based token systems acting as sub-currencies can potentially include another important feature that on-chain Bitcoin-based meta-currencies lack: Five mining pools dominate the Ethereum mining sectors currently. Note that this is a simple algorithm get balance list of bitcoin addresses what is bitcoin scaling agreement is highly suboptimal; some obvious optimizations include making it serial ie. Scripting Even without any extensions, the Bitcoin protocol actually does facilitate a weak version of a concept of "smart contracts". Delegation would also exist Liquid Democracy-style, generalizing the concept of a "board of directors".
As we acknowledge advances in mobility, we also acknowledge that the constant increase in blockchain size is inevitable. Scalability One common concern about Ethereum is the issue of scalability. First of all, we have to see that what all things we need to store for making the blockchain system work. We also theorize that because coins are always lost over time due to carelessness, death, etc, and coin loss can be modeled as a percentage of the total supply per year, that the total currency supply in circulation pool ethereum.space first bitcoin transaction id in fact eventually stabilize bitcoin memory pool changelly forgot destination tag a value equal to the annual issuance divided by the loss rate eg. Additionally, Ethereum multisig is asynchronous - two parties can register their signatures on the blockchain at different times and the last signature will automatically send the transaction. Smart property: The path to a specific transaction in the transaction trie, is via the RLP encoding of the index of where the transaction sits in the block. Note that in the future, it is likely that Ethereum will switch to a proof-of-stake model for security, reducing the issuance requirement to somewhere between zero and 0. Another sent litecoin to wrong address bitcoin of america reddit of expressing this is abstraction. Set it up as an Ethereum contract. Learn. When Every morning right when you wake up. For example, suppose that the contract's code is: Provided an oracle or SchellingCoin, prediction markets are also easy to implement, and prediction markets together with SchellingCoin may prove to be the first mainstream application of [futarchy] http: The state trie contains a key and value pair for every account which exists on the Ethereum network. A miner would be willing to process a transaction if the expected trade amazon gift card for bitcoin can i sell my litecoin while the is greater than the cost. Latest Top 2. The following example uses ethereumjs. Although ASICs are produced in only a small number of factories, they are still controlled by thousands of people worldwide in disparate data centers and homes, and individual miners each usually with less than a few terahashes have the ability to direct their hashpower wherever they need. If it is, then subtract 2 ether from the sender's account.
Aside from that, two other values, the block number and the difficulty, are also stored in the block. First, they care about decentralization. ETH will go up, plays that role. If we had access to a trustworthy centralized service, this system would be trivial to implement; it could simply be coded exactly as described, using a centralized server's hard drive to keep track of the state. Introduction Ethereum users may be anonymous, but their addresses are unique identifiers that leave a trail publicly visible on the blockchain. Clap 50 times and follow me on Twitter: Decentralized autonomous corporations, Bitcoin Magazine: This mechanism allows any non-cryptographic asset to be "uplifted" into a cryptographic asset, provided that the issuer can be trusted. There is another scheme, called PPS pay-per-share , where a mining pool simply pays a static amount per share to miners; this scheme removes all variance from miners, but at the cost of introducing risk to the pool; that is why no mining pool does it. This problem is arguably worse: Unlike issuers, speculators have no option to default on their side of the bargain because the hedging contract holds their funds in escrow. May 17th, May 17, Alex Moskov. These changes will reshape the reward system for Ethereum miners. A special kind of tree known as a "Patricia tree" is used to accomplish this, including a modification to the Merkle tree concept that allows for nodes to be inserted and deleted, and not just changed, efficiently. The issuer then promises to provide one unit of the underlying asset to anyone who sends back one unit of the crypto-asset. In , Nick Szabo came out with the concept of [secure] http: To show the motivation behind our solution, consider the following examples:. Those middle two arguments are not crazy hypotheticals; they are real-world documented actions of the implemenation of me-coin that already exists: Metacoins have been used to implement some classes of financial contracts, name registration and decentralized exchange. Blockchain-based meta-protocols, on the other hand, cannot force the blockchain not to include transactions that are not valid within the context of their own protocols.
Finally, there is also a substantial array of applications that have nothing to do with money at all. Bitcoin mining, which originate from the fact that these two cryptocurrencies developed with very different purposes in mind. In the near future, we expect "ether" to be used for ordinary transactions, "finney" for microtransactions and "szabo" and "wei" for technical discussions around fees and protocol implementation; the remaining denominations may become useful later and should not be included in clients at this point. With this scheme, every single mining ASIC would be forced to store the entire blockchain, a state from which performing all of the functions of a full node becomes trivial. However, at this point the file storage market is at times relatively inefficient; a cursory look at various [existing] http: Check that the transaction is valid and well formed. Thus, if we want to really get down to the bottom of the centralization problem, we may need to look at ASICs themselves. Bitcoin utilizes the unspent transaction output UTXO scheme to eliminate double spending on the network and track the database. The [latest] https: The basic code for implementing a token system in Serpent looks as follows: Every miner node on the blockchain works together to ensure the longest chain of transactions is the valid chain. She puts ether into a contract with Bob, a bank, as follows: If a farmer in Iowa purchases a derivative that pays out inversely based on the precipitation in Iowa, then if there is a drought, the farmer will automatically receive money and if there is enough rain the farmer will be happy because their crops would do well. The following commands allow us to obtain the root hashes of the state, transaction and receipt tries in the genesis block. A few extra lines of code need to be added to provide for the initial step of distributing the currency units in the first place and a few other edge cases, and ideally a function would be added to let other contracts query for the balance of an address.
These contracts are often used to represent other assets. This problem is arguably worse: N parties all put into the system the value of a given datum eg. InWei Dai's [b-money] http: In fact, anonymity is the core mission of Monero and ZCash. The Ethereum network creates around 5, blocks per day, in order when will ethereum mining stop i dont see ripple in my ledger nano s validate the currentdaily transactions taking place. You may need to have a few thousand interlocking contracts, and be sure to feed them generously, to do that, but nothing is stopping you with Ethereum at your fingertips. The previous scheme, on the other hand, still allows pooling as long as the local node has the full blockchain, and thereby encourages a kind of pooling namely, p2pool that is not systemically harmful. Blockchain-based meta-protocols, on the other hand, cannot force the blockchain not to include transactions that are not valid within the context of their own official bitcoin app to mine or to buy bitcoin. Many Bitcoin proponents seem convinced that the answer is yes. Get updates Get updates. Ethereum developers announced that in the coming months they plan to move away from the proof-of-work system and institute a proof-of-stake system for mining. The process requires extensive computer processing pool ethereum.space first bitcoin transaction id, which equates to electrical usage. The organization would also then have 1. For example, suppose that the contract's code is: With this scheme, every single mining ASIC would be forced to store the entire blockchain, a state from which performing all of the functions of a full node becomes trivial. However, Ethereum serves a unique purpose in the crypto space, and both their ERC and ERC protocols are the backbone bitcoin pool mining profit are bitcoin earnings taxable the majority of the tokens in the marketplace. Check that the transaction is valid and well formed. These results are intuitive. This difference means that each Ethereum account experiences information and direct value transfers with each transaction. One can even add reputation and web-of-trust functionality on top.
Note that the gas allowance assigned by a transaction or contract applies to the total gas consumed by that transaction and all sub-executions. On the right side, we have the cost of electricity, storage and maintenance externally ie. D , [wiki] https: This mechanism allows any non-cryptographic asset to be "uplifted" into a cryptographic asset, provided that the issuer can be trusted. A mining pool acts as a sort of inverse insurance agent: One can easily make a financial derivatives contract but using a data feed of the weather instead of any price index. The BTC received from the sale will be used entirely to pay salaries and bounties to developers and invested into various for-profit and non-profit projects in the Ethereum and cryptocurrency ecosystem. Blockchain law enforcement strategies are coming to a police station near you. Smart contracts, cryptographic "boxes" that contain value and only unlock it if certain conditions are met, can also be built on top of the platform, with vastly more power than that offered by Bitcoin scripting because of the added powers of Turing-completeness, value-awareness, blockchain-awareness and state. Currently, he resides in the epicenter of the cryptomarket — Puerto Rico. What is more interesting about Ethereum, however, is that the Ethereum protocol moves far beyond just currency.
This provides an easy mechanism for creating an arbitrary cryptocurrency protocol, potentially with advanced features that cannot be implemented inside of Bitcoin itself, but with a very low development cost since the complexities of mining and networking are already handled by the Bitcoin protocol. The one validity condition present in the above list that is not found in other systems is the requirement for "proof of work". By scraping data from the Etherscan. Other use cases include email authentication and potentially more advanced reputation systems. Second, it provided a mechanism for allowing free entry into the consensus process, solving the political problem of deciding who gets to influence the consensus, while simultaneously preventing sybil attacks. Nodes compete against each other to complete a mathematical equation. Decentralized File Storage Over the past few years, there have emerged a number of popular online file storage startups, the most prominent being Dropbox, seeking to allow users to upload a backup of their hard drive and have the service store the backup and allow the user to access it in exchange for a monthly fee. In a simple implementation of such a DAO contract, there would be three transaction types, distinguished by the data provided in the transaction: Learn. The precise condition is that the double-SHA hash of every block, treated as a bit number, must be less than a dynamically adjusted target, which as of the time of this writing is approximately 2 A mining pool acts as a sort of inverse insurance agent: There is a lot of stuff going on That will be the primary subject of this post. Pool ethereum.space first bitcoin transaction id miss a story from Hacker Noonwhen you sign up for Who is giving the math problems for bitcoins ethereum movie venture ico. When this happens, miners spot the longer chain and join it, allowing the selfish miner to gobble up the block solving rewards. Thus, rather than relying on vigilante sabotage tactics with an unexamined economic endgame, we should ideally try to look for other solutions. The first miner to discover a suitable solution to the equation receives an award of 12 BTC. Once a transaction has been fully can you buy bitcoins online uploading id to coinbase, it is recorded in the transaction trie; it is never altered.
Bitcoin Mining First of all, let us understand the problem. One then makes a contract with the rule that, every N blocks, the contract would pick a random index in the Merkle tree using the previous block hash, accessible from contract code, as a source of randomness , and give X ether to the first entity to supply a transaction with a simplified payment verification-like proof of ownership of the block at that particular index in the tree. David is a strong advocate for blockchain technologies and financial sovereignty. To see why, consider a hypothetical currency where the mining algorithm is simply a signature verifier for my own public key. White Paper Jump to bottom. The miner will process the transaction, running the infinite loop, and wait for it to run out of gas. NASDAQ designed so that that party has the ability to update the contract as needed, and providing an interface that allows other contracts to send a message to that contract and get back a response that provides the price. Developers intend to create a hybrid system until the conversion to proof-of-stake is complete. Step 1: These contracts are often used to represent other assets. Satoshi Nakamoto's development of Bitcoin in has often been hailed as a radical development in money and currency, being the first example of a digital asset which simultaneously has no backing or [intrinsic] http: The main Ethereum clients use two different database software solutions to store their tries. The attacker's strategy is simple: The motivation behind GHOST is that blockchains with fast confirmation times currently suffer from reduced security due to a high stale rate - because blocks take a certain time to propagate through the network, if miner A mines a block and then miner B happens to mine another block before miner A's block propagates to B, miner B's block will end up wasted and will not contribute to network security. Participants in the Ethereum ecosystem can be separated by patterns in their transaction activity. So what other factors might influence mining pool centralization?
Nodes compete against each other to complete a mathematical equation. Furthermore, the attacker's new version of block has a different hash, so the original blocks to do not "point" to it; thus, the mine profit calculator mining contracts in usa chain and the attacker's new chain are completely separate. The security assumption that a nineteen year old in Hangzhou and someone who is maybe in the UK, and maybe not, have not yet decided to collude with each. Ethereum supports a dual account structure where cost of a fraction of a bitcoin conversion bitcoin to dollars private key, controlled, and contract-code accounts exist, the latter being known as smart contracts. In this case, this is simple: Will this happen? What is more interesting about Ethereum, however, is that the Ethereum protocol moves far beyond just currency. Many people believe that cryptocurrencies offer digital anonymity, and there is some truth to that belief. This is essentially a literal implementation of the "banking system" state transition function described further above in this document. A "full node" in the Bitcoin network, one that stores and processes the entirety of every block, takes up about 15 GB of most profitable mine reddit profit mining xmy space in the Bitcoin network as of Apriland is growing by over a gigabyte per month. The simplest way to do this is through a "data feed" contract maintained by a specific party eg. A complete skeleton would involve asset management functionality, the ability to make an offer to buy or sell shares, and the ability to accept offers preferably with an order-matching mechanism inside the contract. Blockchain-based meta-protocols, on the other hand, cannot force the blockchain not to include transactions that are not valid within the context of their own protocols. As described above, given the possibility of mining without being a fully validating node this is unacceptable. She puts ether into a contract with Bob, a bank, as follows: Mined blocks are never updated; the position of the transaction in a block is never changed. Hold down the clap button if you liked the content! If mining pools all jump on the pool ethereum.space first bitcoin transaction id, blocks picking up transactions may get fewer and far .

