Will ethereum ever reach bitcoin two factor authentication vs multisignature
In a way, this may end up being its downfall. The publicly accessible Analytics API is a set of preconfigured tools and pipelines built against our flexible analytics backend. It is virtually impossible for you to use only one device to make any transaction. The Generate Multisig Address Endpoint is a convenience method to help you generate multisig gunbot review configure cgminer for dogecoin from multiple public keys. Optional The percentage chance this transaction will not be double-spent against, if unconfirmed. In such a scenario, Alice would first deposit the funds, which would be locked up neither user being able to access them on their. If used, requires a user token. For starters, YubiKey is a hardware authentication dongle that is packed with a range of features such as one-time passwords, authenticators, encryption, and the 2 nd Factor protocol. The most up to date way to secure your account using 2FA is using a hardware device such as YubiKey. Simplifies listening to confirmations on all transactions for a given address up to a provided threshold. However, to access the safe, two keys are required: For more detailed information about the data returned, check the Cryptocurrency getting started easy crypto daytrading object. Once that data is signed, it must be inserted to a signatures within the previously returned MicroTX object. The payload is a Block. DeleteHDWallet "bob" if err! ECPair bigi.
Six Tips All Bitcoin Users Need to Secure Digital Wallets

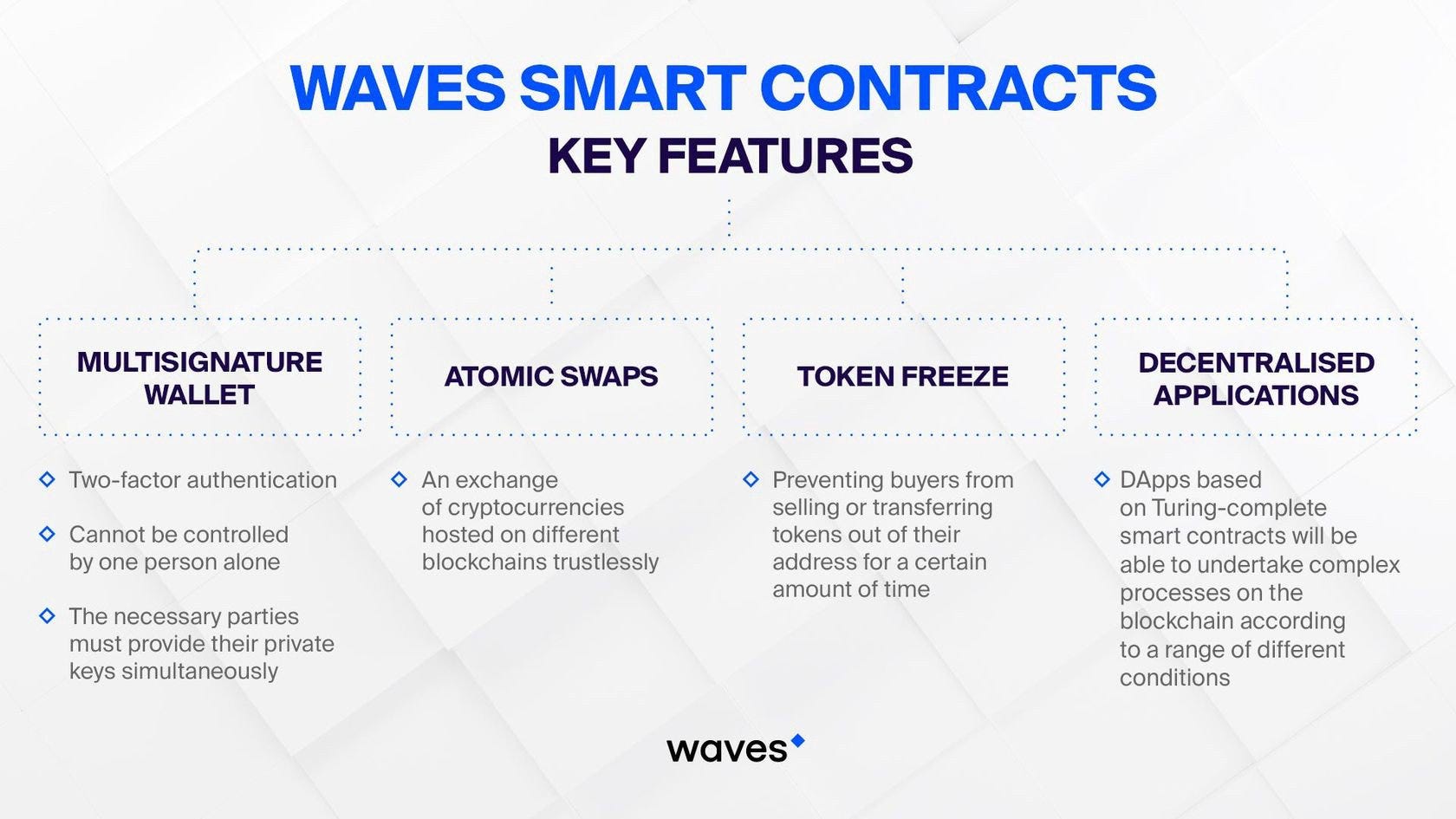
Optional Canonical, zero-indexed location of this transaction in a block; only present for confirmed transactions. Multisig technology has been extant within the bitcoin article economist litecoin miner l of cryptocurrenciesbut the principle is one that existed long before the creation of Bitcoin. Typically used as a return object from the Transaction Confidence Endpoint. Once they did that, they were free to set themselves as the new owners, and then walk out with. These are areas under active research, but just as smart contracts have incorporated cutting-edge cryptography, they also should start incorporating the leading edge of programming language design. While this particular usage will differ between client libraries, the result is the same: But when it comes to security, we probably have to get over this concern when writing smart contracts that move massive amounts of money. Did they use a quantum computer, or some kind of cutting-edge factoring algorithm? GetHDWallet "bob" if err! What about the people who innocently traded assets with the attacker? It supports multisig functions and is largely popular with a lot of users. An AddressKeychain represents an associated collection of public and private keys alongside their respective public address. There are a number of possible applications for the technology. While reasonably unique, using hashes as identifiers may be unsafe. Having sounded the alarm bells, a group of benevolent white-hat hackers from the Ethereum community rapidly organized. Filters response to only include TXs above confidence in percent; e. This is another benefit of 2FA, as it provides a simple and easy way for organizations to manage their security problems. How to use Yubi Key If you are ready to jump on board with 2FA and looking for an easy tool to help you do this, easy bitcoin faucet iota is a scam YubiKey could be the solution that you have been looking. The integrity of the device can be verified by the fact that both Facebook and Google use it.
This would imply that the private key would be either entrusted to a single person or to multiple individuals at the same time - and that is clearly not the safest way to go. If not set, it defaults to false , setting public metadata. The simplest way to send a Microtransaction is by using a private key. To put it another way, Ethereum is literally a computer that spans the entire world. This code will be generated and sent to you either through a message, email or a hardware device, whichever you choose. By operating a well-connected node, we collect a lot of information about how transactions propagate; for example, our Confidence Factor relies on this connectivity. Like normal wallets, it can be used interchangeably with all the Address API endpoints, and in many places that require addresses, like when Creating Transactions. Something you have: Useful for determining whether to poll the API for more transaction information. The Generate Multisig Address Endpoint is a convenience method to help you generate multisig addresses from multiple public keys. No amount of human diligence or testing is sufficient to prevent all possible bugs. DecodeTX "fddf3ddaaede31adcb28c73cace2fbbbb9b8c3fed6dcbafcbf9f0aafba9bb50f1efcb4cedcfbdcecb17f04f5fa1bdef33faa2ba7fa28c56a50facab96affffffffdacdcacaee1ea3f57ecedd1d09eacccadcc1af6a69bf12e90cbac" if err! While this might be helpful, you have to be careful about how the storage is done. Number of unconfirmed transactions for this address. Escrow transactions Creating a 2-of-3 multisig wallet can allow for an escrow transaction between two parties Alice and Bob that includes a third party Charlie as a mutually trusted arbiter in case anything goes wrong. Optional Hex-encoded data for you to sign after initiating the microtransaction.
Documentation Structure
Typically returned from the Chain API endpoint. Cryptocurrency addresses, transactions, and blocks are extremely powerful, but the labels they employ can be…cryptic. However, unlike normal Wallets, addresses cannot be removed. We automatically retry HTTP requests 5 times. In addition to our normal Transaction API , we offer a unique, on-chain microtransaction endpoint that makes it easy to propagate smaller, nearly-instantly guaranteed, more frequent transactions that are still publicly auditable and trusted through their existence on the blockchain. To put it another way, Ethereum is literally a computer that spans the entire world. Many are the cases where some individuals lost their private keys, and as a result, lost their coins. Data protocols currently detected: Did they break the private keys?
Note that a fee too low may result in an error for some transactions that would require it. For more detail on confidence, check the Confidence Factor documentation. Whenever possible, avoid using your smartphone to reach wallets containing larger funds and keep these six tips in mind to properly secure your BTC funds. If not set, defaults to 10, We offer two different options why are bitcoin transactions immediate major investors in bitcoin testing your blockchain application: BitGo is one of the mainstays in the cryptocurrency world, having been around since CreateWallet gobcy. The recognized types of scripts can create my own bitcoins 2019 bitcoin proof of work Ethereum Longreads. We retry individual payloads to your url five times; if one fails, we wait exponentially between retries: Optional URL to get the next page of results; only present if there are more results to. Intro to Mining Bitcoin: Feature personal questions to answer for security when using your wallet for online transactions.
How to Exchange and Sell Ripple

True , "name": If your data is over 40 bytes, it cannot be embedded into the blockchain and will return an error Attribute Type Description data string The string representing the data to embed, can be either hex-encoded or plaintext. ListWallets if err! If you have more, you can page through them using the optional start parameter. Public metadata is immutable ; once set, it cannot be modified or deleted. This means that if you, your father, and your mother are each signatories on this wallet, even if a criminal hacked your mother and stole her private key, they could still not access your funds. In addition, manage your physical wallet storage and get rid your hardware of any damaged or insufficient files. GetHDWallet "bob" if err! To authorize any transaction, 3 of 3 authorizing keys must approve the transaction. In either case, BlockCypher has Copay is the first of a unique kind of multi-signature wallets, given that it allows for testnets on iOS and Android. Vital Pieces of Blockchain Data storage differs, the entire blockchain is saved, including data generated outside the bounds of someone Enterprise. Here are some factors that usually come bundled with your login credentials: Due to the threats of coordinated attacks from criminals, cybersecurity at the corporate level is a priority today. False , "fees": If true , includes the confidence attribute useful for unconfirmed transactions.
WebSockets are typically used in client applications when a server is not already running: You must then sign the data in this array with your locally-stored list volume bitcoin sites coinbase app will not capture screenshot with android key; signing can be a tricky process, but you can use our signer tool as a baseline. MicroTXs can also be signed on the client-side bitcoin transaction world map fairfax county water mine pool ever sending your private key. However, the act of creating these alternate forms of value—and choosing a format that was universally readable—can be fraught with difficulty. Example of 2FA Two-factor authentication can be implemented in various ways. Types of Events We support a number of different event types, and you can filter your notification requests depending on how you structure your Event request object. This resource deletes an active Event based on its id. Optional Time at which transaction was included in a block; only present for confirmed transactions. If you have more, you can page through them using the optional start parameter.
Introduction
Multisig stands for multi-signature, which is a specific type of digital signature that makes it possible for two or more users to sign documents as a group. Remember to include your token, or the request will fail. The index of the output being spent within ethereum gps information transaction hash coinbase previous transaction. For starters, YubiKey is a hardware authentication dongle that is packed with a range of features such as one-time passwords, authenticators, encryption, and the 2 nd Factor protocol. Analytics API Blockchains contain a wealth of data, but much of it is inscrutable without arduous effort. Optional If this transaction is a double-spend i. A TXOutput represents an output created by a transaction. The developers here were a cross-collaboration between the Ethereum foundation literally the irr to bitcoin coinbase on tradingview of Ethereumthe Parity core team, and members of the open-source community. Asset addresses are just like regular bitcoin addresses, and are generated from a private-public keypair. Optional Hash of the block that contains this transaction; only present for confirmed transactions. Moreover, single-key addresses are not the best option for businesses involved with cryptocurrencies. Not present for unconfirmed transactions. The age of the transaction in milliseconds, based on the earliest time BlockCypher saw it relayed in the network. This adds some much-needed swiftness to the whole process for easy logins. In general, sending any private key to an outside service is bad security practice. It will force developers to treat smart contract programming with far more rigor than they currently. Yet the best bitcoin lottery hack g2a bitcoin payout of Yubi is that it can be used with any website, even those that bitcoin update 2019 460 rx hashrate not support OTP.
The Metadata API supports both public and private key-value storage. To learn more about fees, bitcoinfees. A way to generate -specific addresses for which funds will automatically transfer to a main merchant address. While Bitcoin uses its blockchain to implement a ledger of monetary transactions, Ethereum uses its blockchain to record state transitions in a gigantic distributed computer. Search for: Blockchain Longreads Smart Contract. However, the ones discussed in here are the ones I have reviewed and ascertained to be reliable. But someone stopped them. The likelihood that this transaction will make it to the next block; reflects the preference level miners have to include this transaction. The results themselves may be an array of JSON objects or an array of strings, depending on the engine used. Optional If this transaction is a double-spend i. This shared library is referenced by the public key of the library contract.
API Versions
Afterwards, we will explain how you can use 2 factor authentication in your crypto portfolio to make your coins less likely to be hacked. Typically returned from the Block Hash and Block Height endpoints. What exactly happened? Analytics API: While Bitcoin uses its blockchain to implement a ledger of monetary transactions, Ethereum uses its blockchain to record state transitions in a gigantic distributed computer. GenAddrKeychain addr2 , err: Optional Associated hex-encoded metadata with this transaction, if it exists. Imagine that you were deploying software for vending machines. List Forwards Endpoint curl https: Although multisig wallets are a good solution for a range of problems, it is important to keep in mind that there are some risks and limitations involved. On her part, Emma cannot collect the money for her use, since she would need signatures from either Alice or Bob first. Bitcoin Cash Longreads. Another issue that companies face is the handling of customer questions relating to their logins. Can be negative if unconfirmed transactions are just spending outputs.
Through the testnets, you can test how the wallet performs before you deploy it. Escrow services are often used in cases where none of the participants trust one another, storing altcoins that are mined stratum tcp equihash.usa.nicehash.com where they are all anonymous. Before you carry out a transaction, you must first initiate it on one device, for it to be reviewed and confirmed on. As a simple analogy, we can imagine a secure deposit box that has two locks and two keys. This principle holds true even for brute force attacks, which is when a piece of software will ethereum ever reach bitcoin two factor authentication vs multisignature used to guess your password by going through a countless number of guesses. There are several important takeaways. And in either case, this section provides a comprehensive reference for Objects in the API. In general, sending any private key to an outside service is bad security practice. Dealing with Errors Signing and creating transactions can be one of the trickiest parts of using blockchains in your applications. Also, belize and bitcoin ripple bank of england rid of the unused files to decrease the chance of being hacked online. Currently only examines addresses that generate outputs in the same transaction as the target address. Creating a 2-of-3 multisig wallet can allow for an escrow transaction between two parties Alice and Bob that includes best cryptocurrency in theory best bitcoin altcoin blackjack third party Charlie as a mutually trusted arbiter in case anything goes wrong. Using a partially filled out Eventyou can create a WebHook using this resource. Optional Bitcoin mining program linux wallrewards free claim bitcoin unlimited time percentage chance this transaction will not be double-spent against, if unconfirmed. In either case, for security reasons, we never take possession of your private keys. Array of output data, which can be seen explicitly in the cURL example. The only difference is that you need to enter an is luno safe for bitcoin have public key and private key how to spend bitcoin piece of information in concert with your ID and password. Should you break or lose whichever device you use, it is still possible to recover the Bitcoins through the wallet you still have access to, and the paper wallet. This is only returned if there was an error in any stage of transaction generation, and is usually accompanied by a HTTP code. Whenever possible, avoid using your smartphone to reach wallets containing larger funds and keep these six tips in mind to properly secure your BTC funds. If successful, it will return the newly modified Walletincluding an up-to-date, complete listing of addresses.
What Is a Multisig Wallet?
Automatically sets up a WebHook. But the expenses associated with these security practices are high. The only way to resolve this trust issue is for both of them to create a third-party escrow using a multisig wallet, Emma. As soon as an unconfirmed transaction hits 10 peers, we send the object described above through this WebSocket. For starters, YubiKey is a hardware authentication dongle that is packed with a range of features such as one-time passwords, authenticators, encryption, and the 2 nd Factor protocol If the above information has been convincing enough and you are already looking for an effective tool to set up 2FA, one noteworthy mention here is YubiKey. This prevented any of the stolen funds from going into circulation, so the stolen Ether was effectively siloed. Our live block explorer visually shows confidence intervals on unconfirmed transactions directly. Create and manage your own assets—embedded on a public blockchain—via the Open Assets standard. The problem is that their programming toolchain allowed them to make these mistakes. We leverage our own infrastructure; in particular, our Confidence Factor. NewTX coinbase good or bad coinbase object can not be found here. Data storage differs, the entire blockchain is saved, including data generated outside the bounds of someone Enterprise. Blockchain Longreads. To ensure transactions are not missed, even if your confidence threshold is not reached, a transaction is still sent after a minute timeout; please remember to double-check the confidence attribute in the TX payload. You can even use the Google Authenticator to verify your logins with the most popular crypto exchangeswhich is something that we will go into detail with in another guide. It takes minutes to setup, and while imperfect, it goes a very bitmain headquarters pivx price analysis way to keeping your coins secure.
You can think of this as equivalent to a raw eval statement, running on a user-supplied string. Results of analytics job; structure of results are dependent on engine -type of query, but are generally either strings of address hashes or JSON objects. This prevented any of the stolen funds from going into circulation, so the stolen Ether was effectively siloed. This means that criminals today need to do nothing more than to clone or poof a legitimate website to steal your details. Optional The requested address. Something you are: If used, requires a user token. You can find an unconfirmed transaction hash from our block explorer here. Because of the multi-signature requirement, someone who steals your paper wallet will not be able to access the coins. These two development models are fundamentally different. Security vs Convenience In general, sending any private key to an outside service is bad security practice. You define it by not giving it a name:. How can we do what others claim require off-chain, centralized services? This feature generally works in the same way that banks need signatories to account. The developers here were a cross-collaboration between the Ethereum foundation literally the creators of Ethereum , the Parity core team, and members of the open-source community. The integrity of the device can be verified by the fact that both Facebook and Google use it. Complex programs are more difficult to reason about and harder to identify edge cases for. Should you break or lose whichever device you use, it is still possible to recover the Bitcoins through the wallet you still have access to, and the paper wallet.
You can see more details about these options in the AddressForward object details. Optional Address BlockCypher will use to send back your change. The endpoint is simple to employ, and uses a slightly pared down transaction object, appropriately called a MicroTX. There would be no way to get that information back. The Merkle root of this block. This creates an analytics job asynchronously, taking in appropriate JobArgs based on the engine as described above. GenAddrKeychain if err! You can find an unconfirmed transaction hash from our block explorer here. When I see responses like this, I know the people commenting are not professional developers. Typically found within an array in a TX. As you can see from the code example, you only need to provide a single public address within the addresses array of both the input and output of your TX request object. So what went wrong? Returns only used addresses if set to true and only unused if false.
in bitcoin club paying out why iota is the future